Review sensitive data files
The sensitive data management module allows you to manage the data exposure risks associated with the content of your files. The sensitive files health check can be green when compliant and red when some files have a risk to be reviewed.
If they contain confidential or secret data, you might want to take action by either removing the file, mark it as a false alarm or justify the need to keep it in its current location.
Steps
1. Review the sensitive data types
First, you can review the data types associated to the highest sensitive data risks and the discovery date when it has been scanned. By selecting a file in the list, you can view the sensitive data details and decide to take action on this risk.
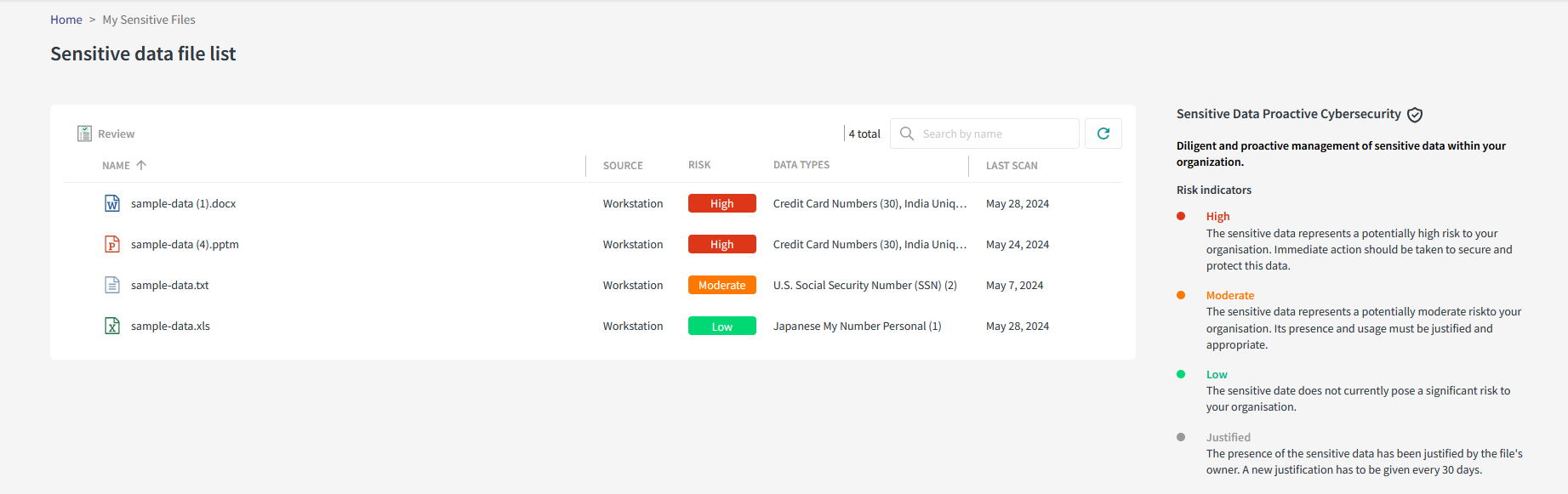
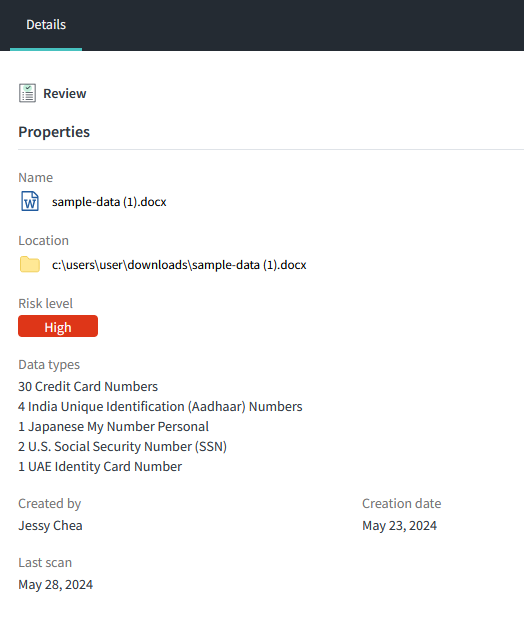
2. Take action on the data sensitive file
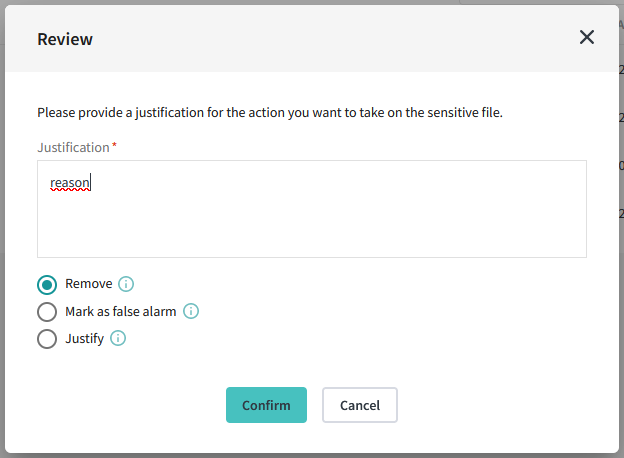
Once the sensitive data types have been reviewed, an action can be taken to either remove or keep the risky file. A comment will be helpful to anotate the decision associated to each file.
Here are the options available:
1-Remove file : The file will no longer be accessible. This action eliminates the risk associated with the identified sensitive data.
2-Mark as false alarm : Report an incorrect detection of sensitive data in a file. Your administrators will review the document and your justification.
3-Justify file : Provide a justification for keeping this file at the current location. Your administrators will review the document and your justification. Meanwhile, the file will remain accessible.
What’s next?
All justifications can be reviewed later and discussed with the data guardian or owner to understand the risk associated to each data type.