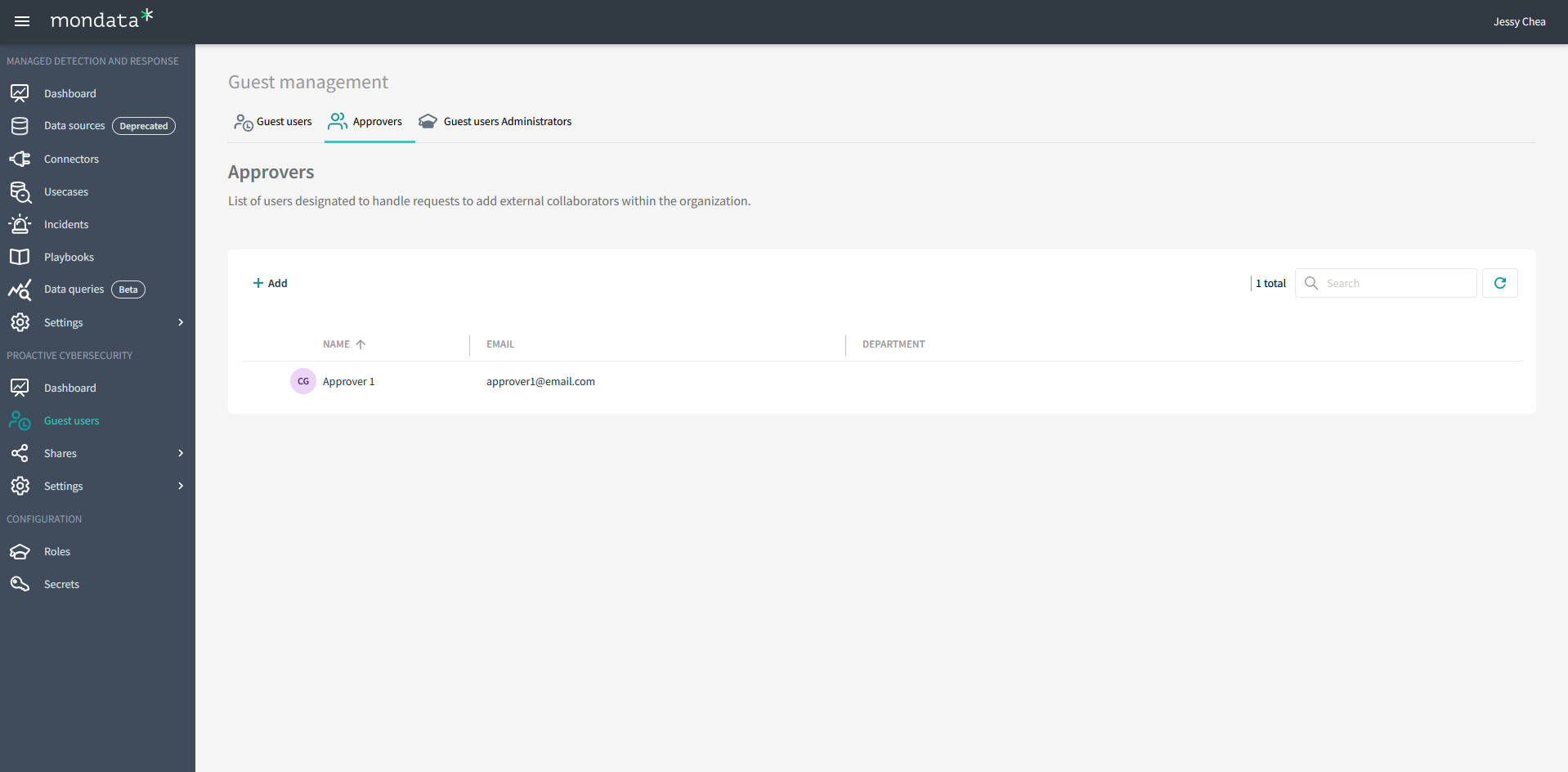
Approvers
What are they?
When internal users want to collaborate with external users, they must first invite them to join their organization. However, in accordance with security best practices, adding external collaborators to the company's tenant is not available to everyone; only users with the appropriate roles are allowed to do so. Generally, these users are from the IT department.
Unfortunately, IT staff often lack context to judge the relevance of the request. This leads to a lengthy and tedious verification process with individuals who can confirm the legitimacy of the request.
MD.ECO proposes a simple way to relieve the IT department by redistributing responsibility to individuals more familiar with the various segments of the organization. Requests are therefore submitted through a simple process via the request system to ensure the legitimacy and efficiency of processing invited collaborators.
The list of approvers allows us to identify all managers responsible for approving requests to add external users by Proactive Cybersecurity users.
Contextualization
Similar to the resource approvers, when contextualization is enabled, an extra column becomes accessible for each manager. In the case of a group, this column represents all the teams included in that group. When users go through the process of inviting a guest, they will only be presented with managers from their own team.
Therefore, if contextualization is activated, please make sure at least one manager is available for each team.
Who?
Users that can be guest managers are users that have the Guest Inviter role in their MS365 tenant.
Groups
Similar to resource approvers, it is also feasible to designate an entire security group as a guest manager. When users embark on the process of inviting an external collaborator, they will encounter the complete list of users without being aware that these users originate from a security group.