AWS Security Hub
AWS Security Hub is a cloud security service that automates security checks and aggregates security alerts in a central location. The service performs best practice validation against your security settings, aggregates alerts, and automates the remediation of non-compliant security settings.
To learn more about the service see the AWS Security Hub documentation.
Prerequisites
- Administrator role in AWS allowing you to configure Security Hub accounts and services
- "Organization Admin" role in MD.ECO
- AWS Security Hub configured in your environment
- The Security Hub delegated administrator account is referred to in this document as
{{SecurityHubAdministratorAccountID}} - Findings must be aggregated in a region designated as
{{AggregationRegion}}in this document
- The Security Hub delegated administrator account is referred to in this document as
- An S3 bucket created following the procedure Ingestion by S3 Bucket
- Referred to in this document as
{{S3SecurityHubAuditBucketName}}
- Referred to in this document as
Security Hub Recommendations
- It is recommended to activate the FSBP repository, it contains the controls relevant to the usecases proposed by Mondata: AWS Standard on Fundamental Security Best Practices (FSBP)
- AWS Cloud Config must be configured to enable discovery of resources required for Security Hub checks: AWS Config Resources needed to generate check results
- It is recommended to use the automatic deployment of Security Hub through integration with the management of the AWS organization, this allows the systematic addition of new accounts in Security Hub: AWS Security Hub Configuration
Functioning
Export of "findings" to an S3 bucket
The integration between AWS Security Hub and Mondata is done via an S3 bucket. Several operations are required at the AWS stack level in order to automatically export data from AWS Security Hub to the integration bucket.
To do this, simply construct the following message transformation chain in the region responsible for aggregation only.
Solution diagram


Configuration steps
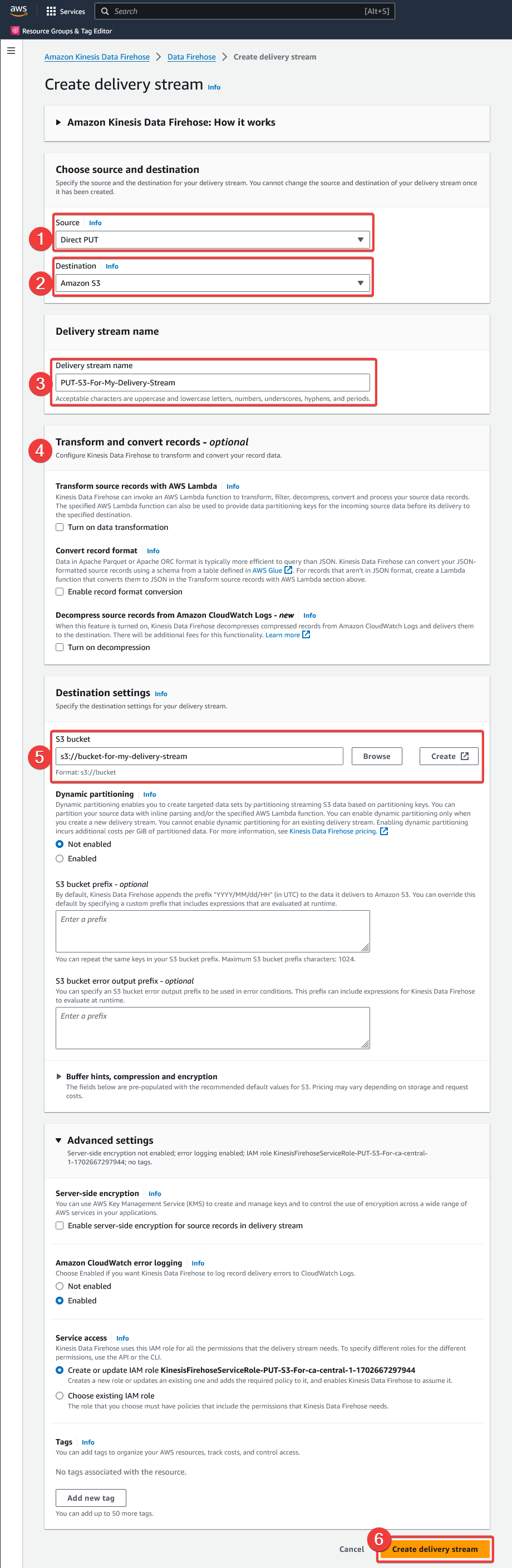
Kinesis Firehose configuration
Create a delivery stream in Kinesis.
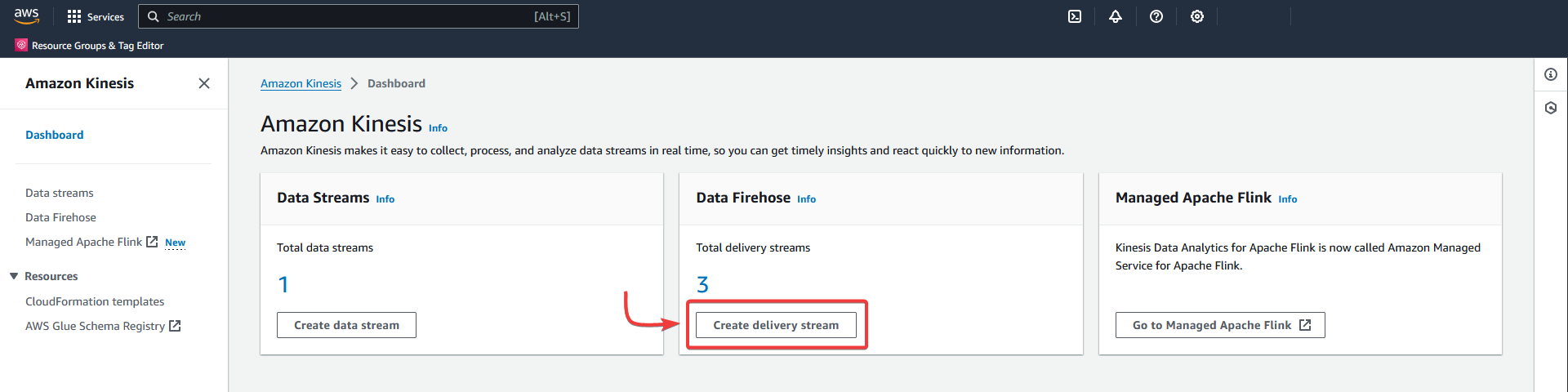
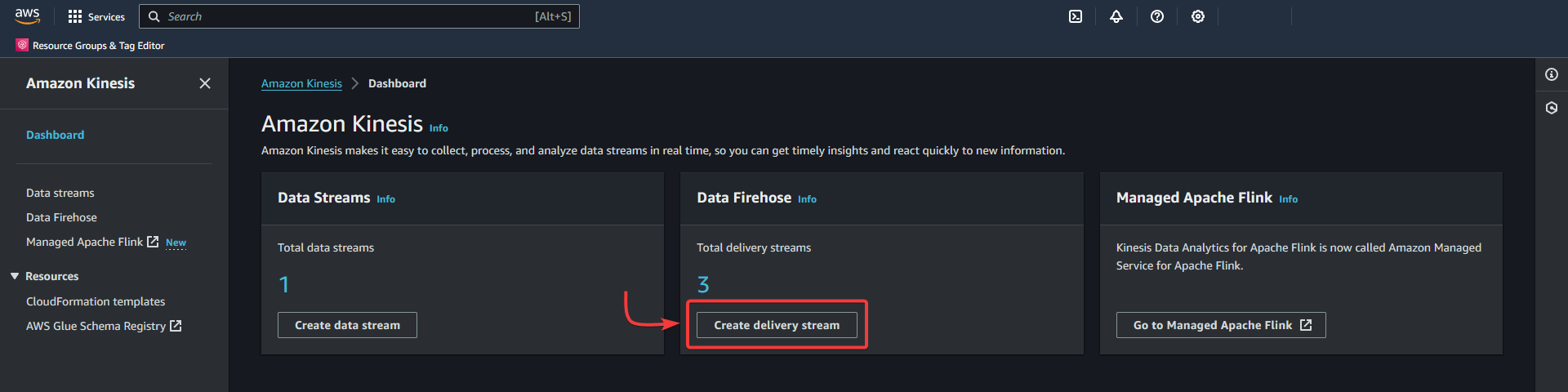
Or
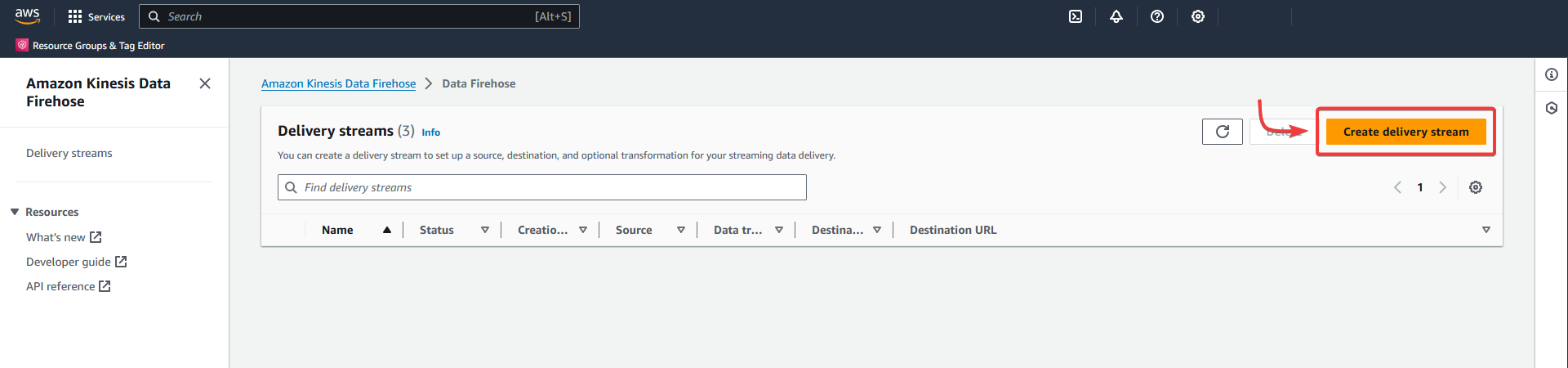
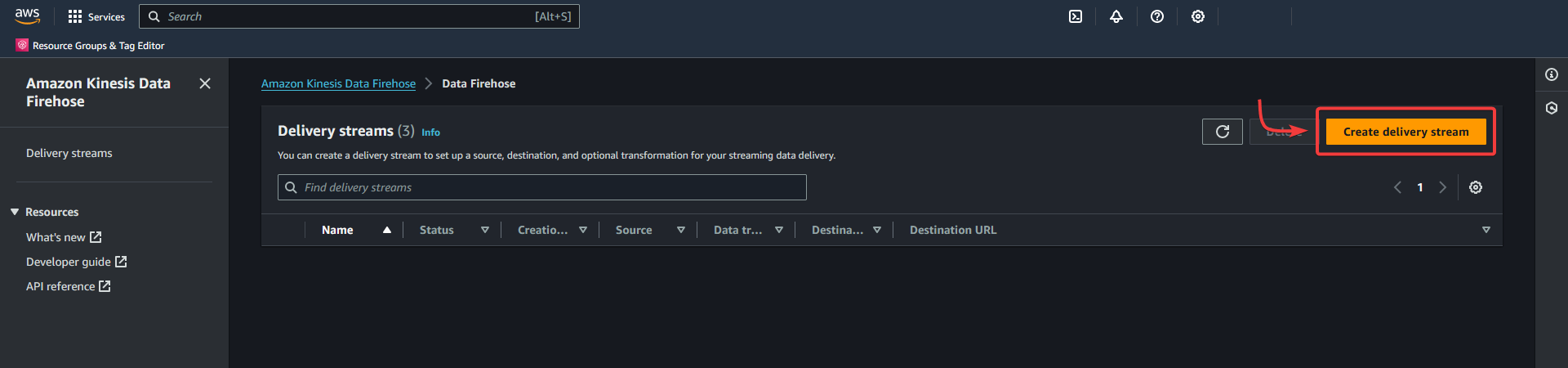
Data Firehose - Create delivery stream
- Choose the "Direct PUT" source
- Choose the "Amazon S3" destination
- Choose a descriptive delivery stream name and keep it noted for the Kinesis Firehose subscription filter creation
- Keep the default options for the "Transform and convert records" category
- Under "Destination parameter", select the S3 bucket
{{S3SecurityHubAuditBucketName}}previously created - Leave the default values for the other configurations and click on "Create delivery stream"
Creating the delivery stream may take a few minutes.
AWS - Kinesis Data Firehose - Create a Delivery Stream
EventBridge configuration
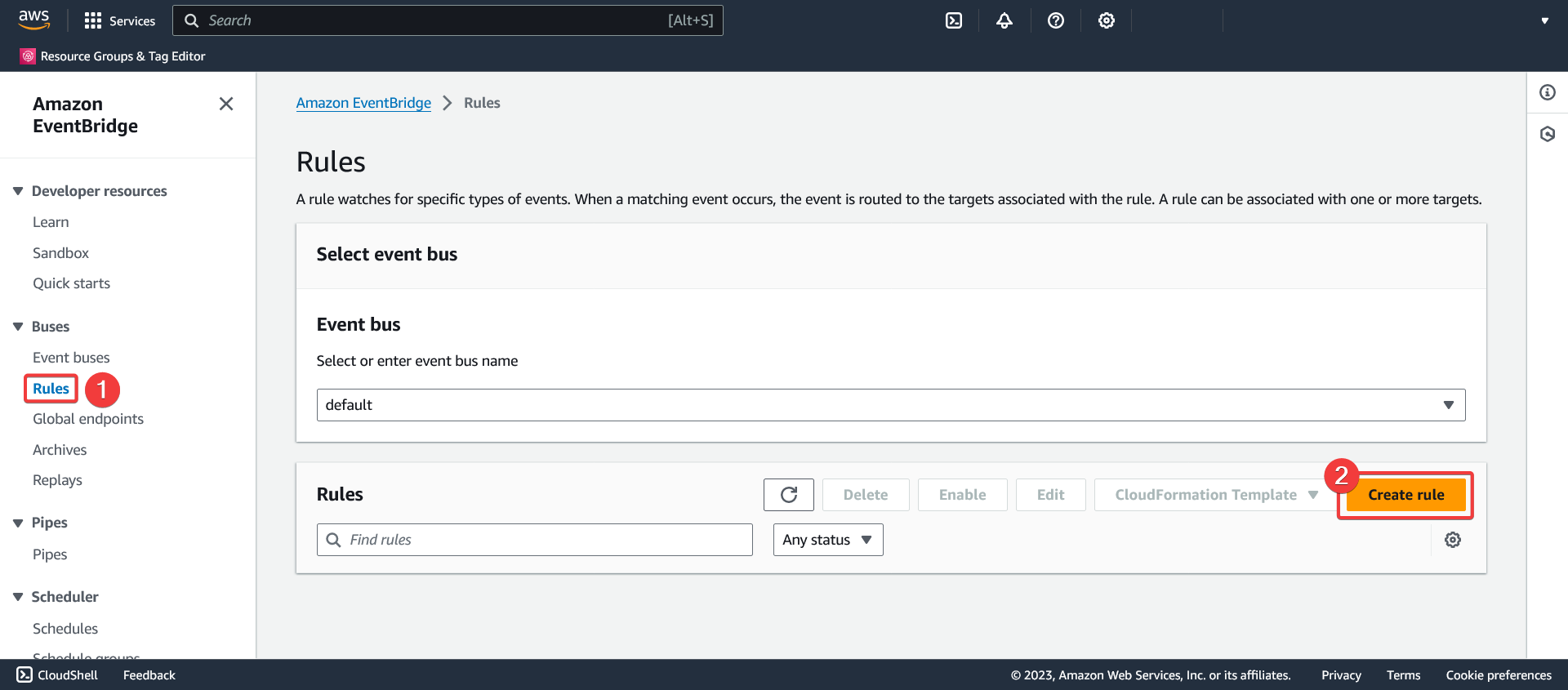
The next step is to create an EventBridge rule between Security Hub and CloudWatch.
- In EventBridge, head to the "Rules" section under the "Buses" category
- Click on the "Create rule" button
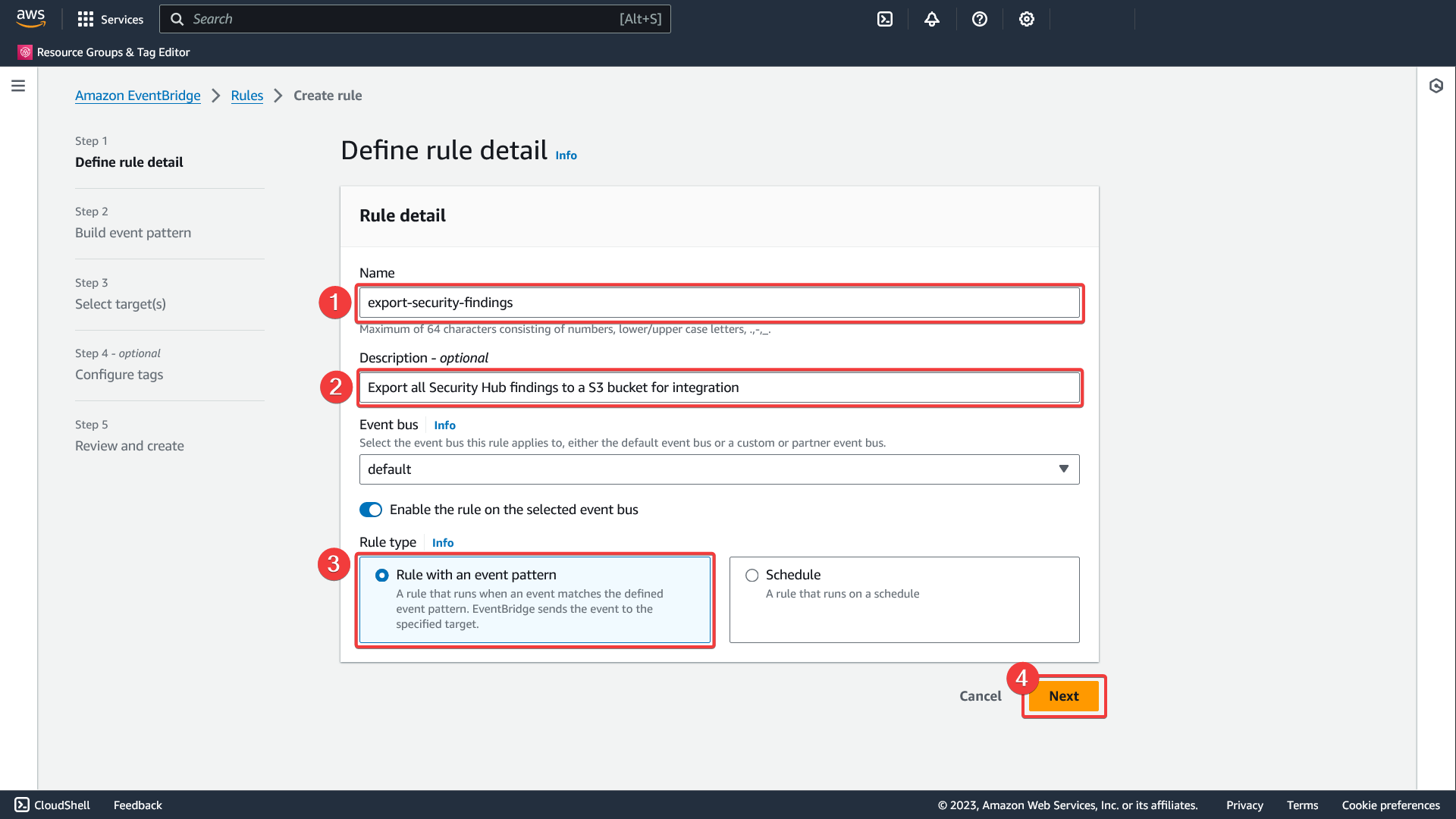
Create rule - Define rule details
- Give the rule a meaningful name
- Give the rule a meaningful description
- Select the rule type "Rule with an event pattern"
- Click Next"
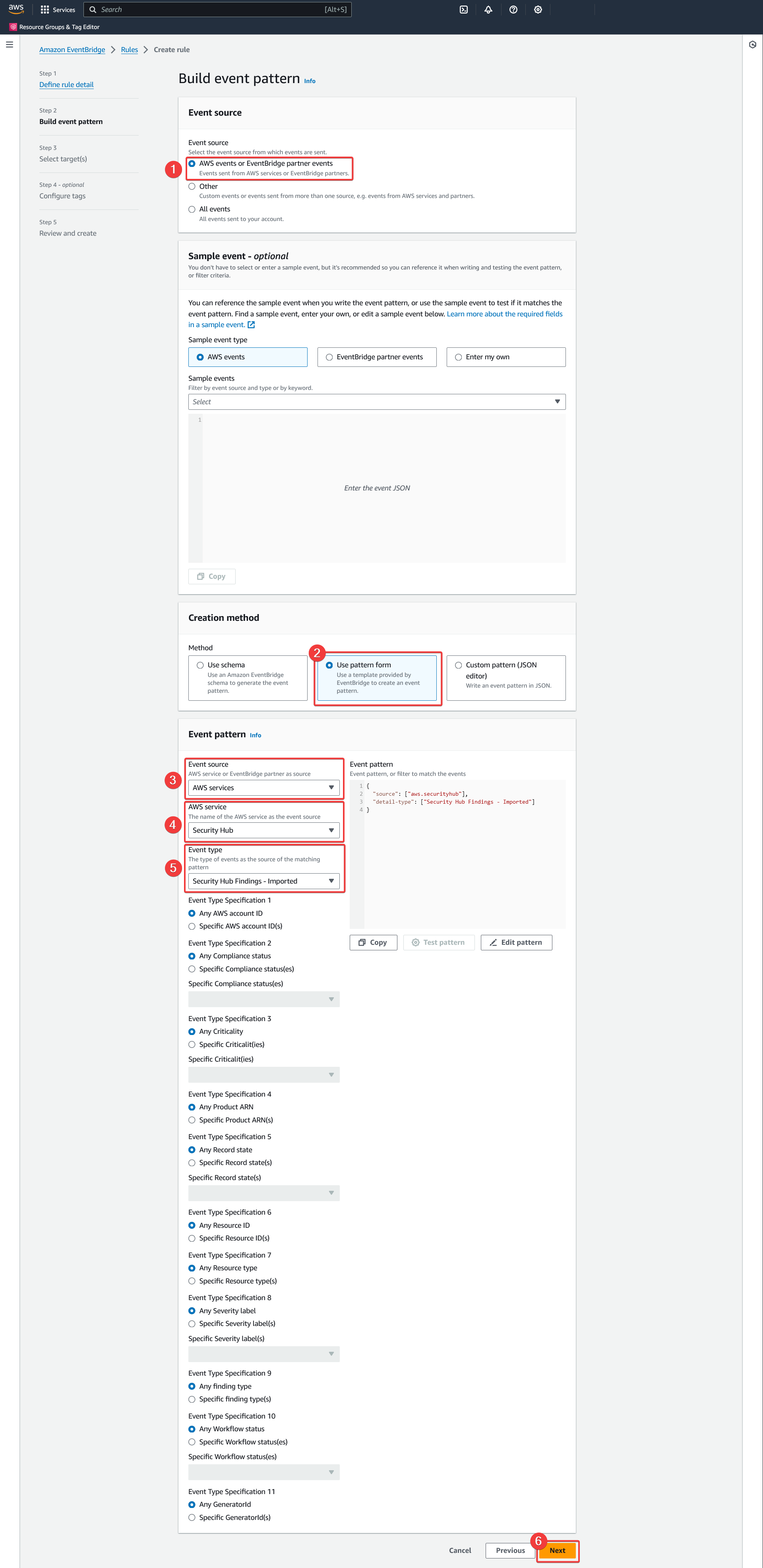
Create rule - Build event pattern
- Select the source "AWS Events [or EventBridge partner events]"
- Select the creation method "Use pattern form"
- Select the "AWS Services" event source
- Select the "Security Hub" AWS Services
- Select the "Security Hub Findings - Imported" event type
- Leave the other values as default and click "Next"
AWS - Amazon EventBridge - Rules - Create rule - Build event pattern
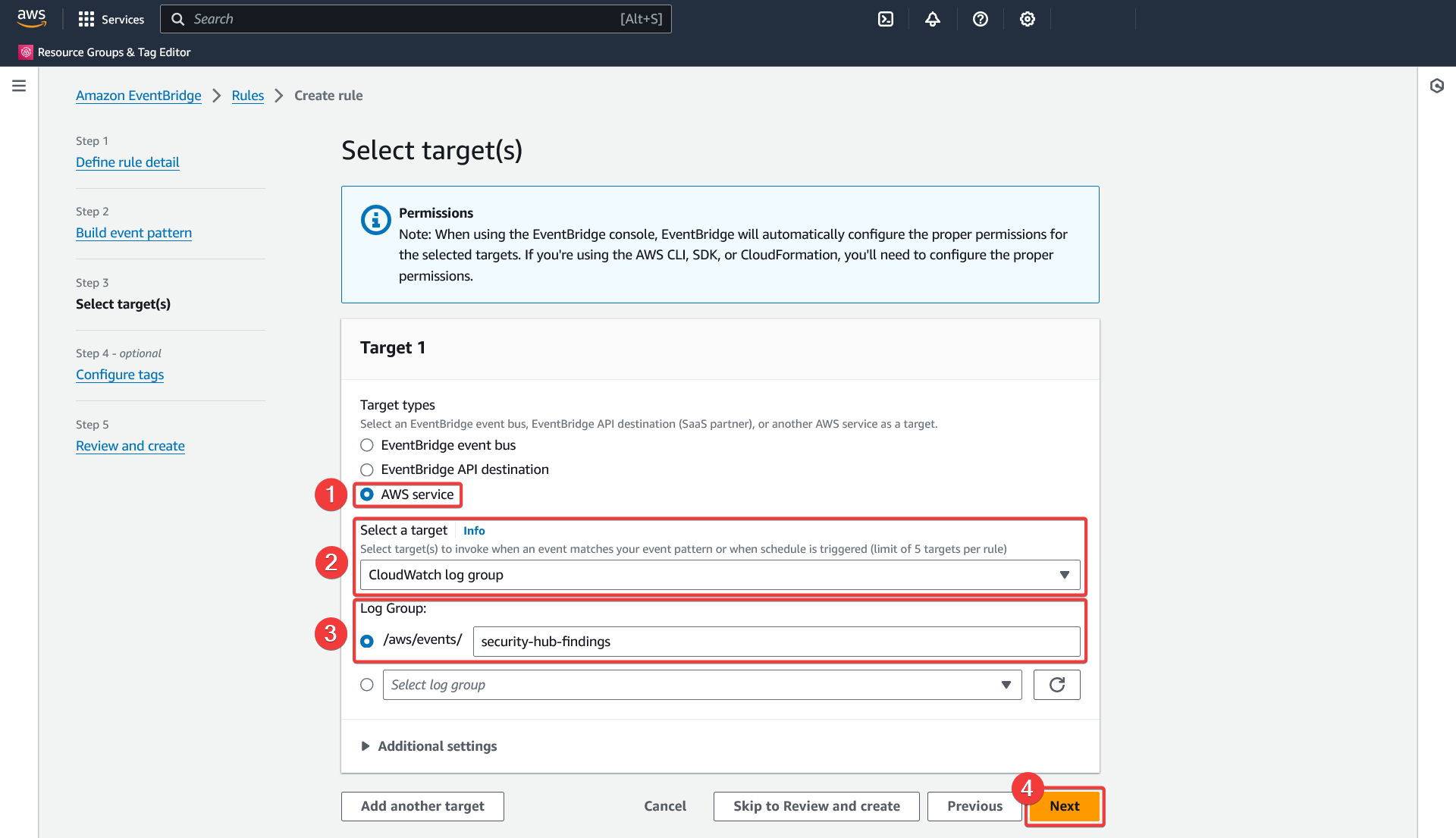
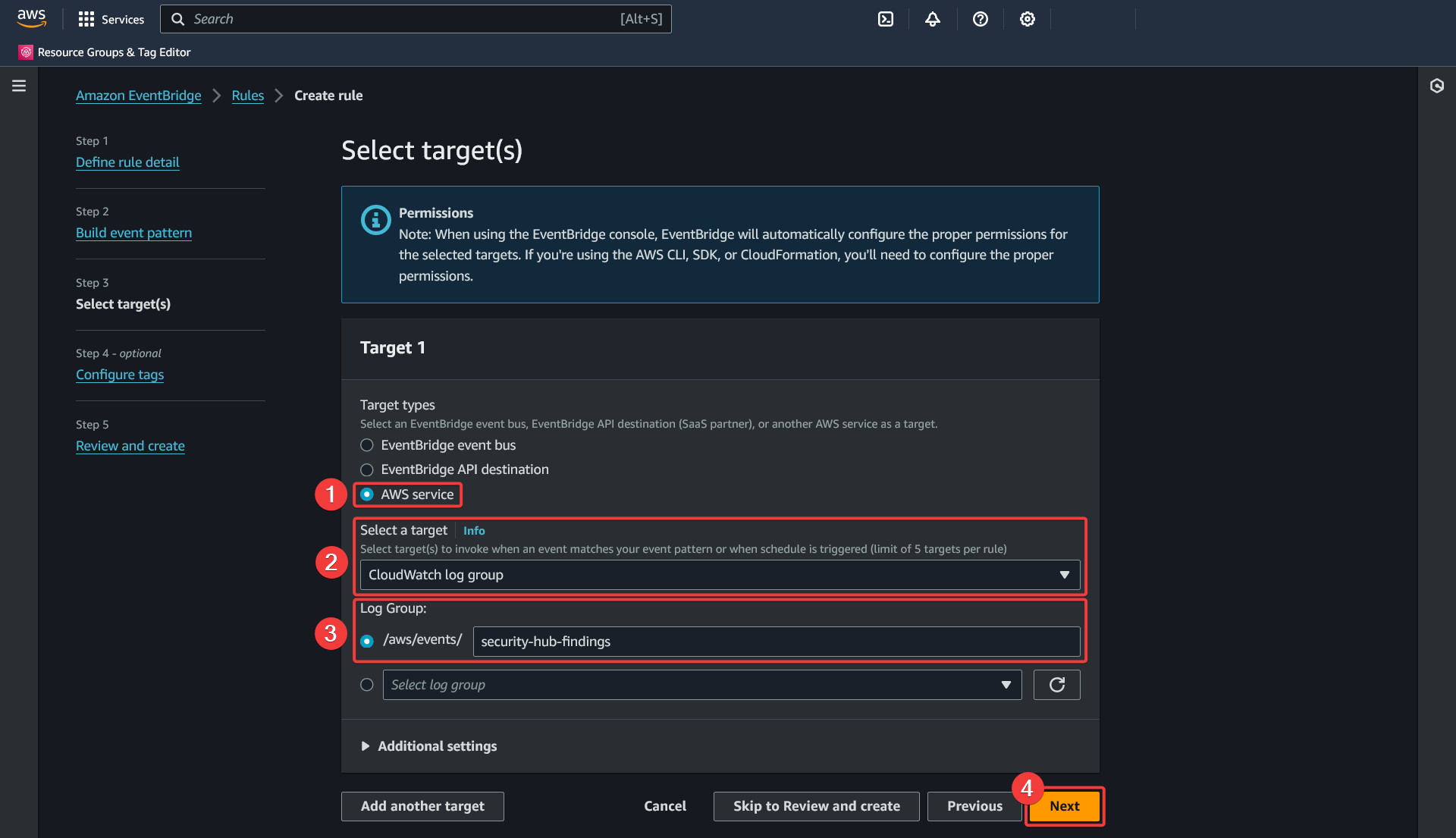
Create rule - Select target(s)
- Select the "AWS Service" target type
- Select the "CloudWatch log group" target
- Choose a descriptive name for the new log group and keep it noted for the Kinesis Firehose subscription filter creation
- Keep "Additional settings" as default and click "Next"
Complete the configuration and create the rule.
CloudWatch configuration
Before you can configure CloudWatch, a role and its policy must first be created for it in IAM.
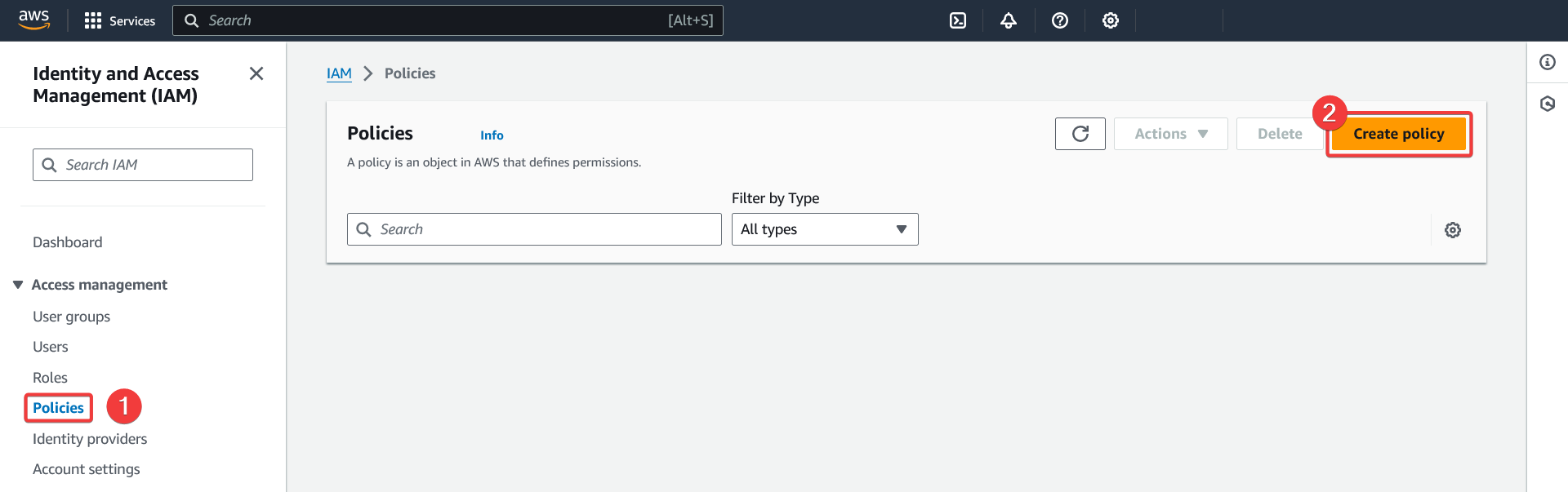
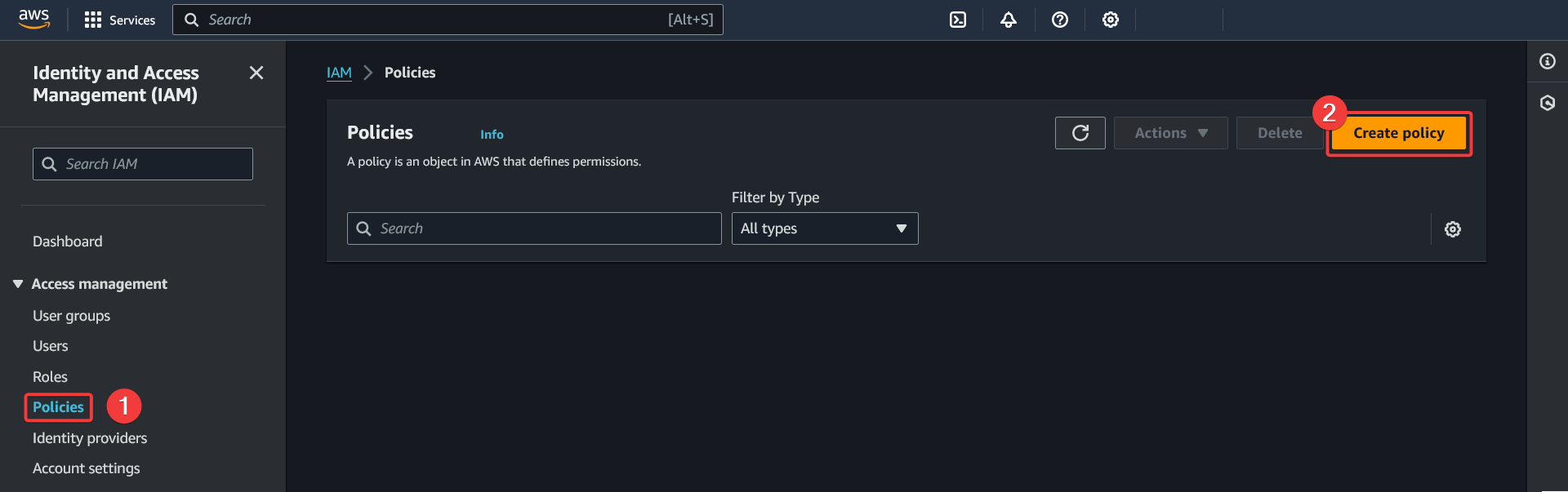
Creating an IAM policy for CloudWatch
- Go to the "Policies" section of the IAM service
- Click "Create policy"
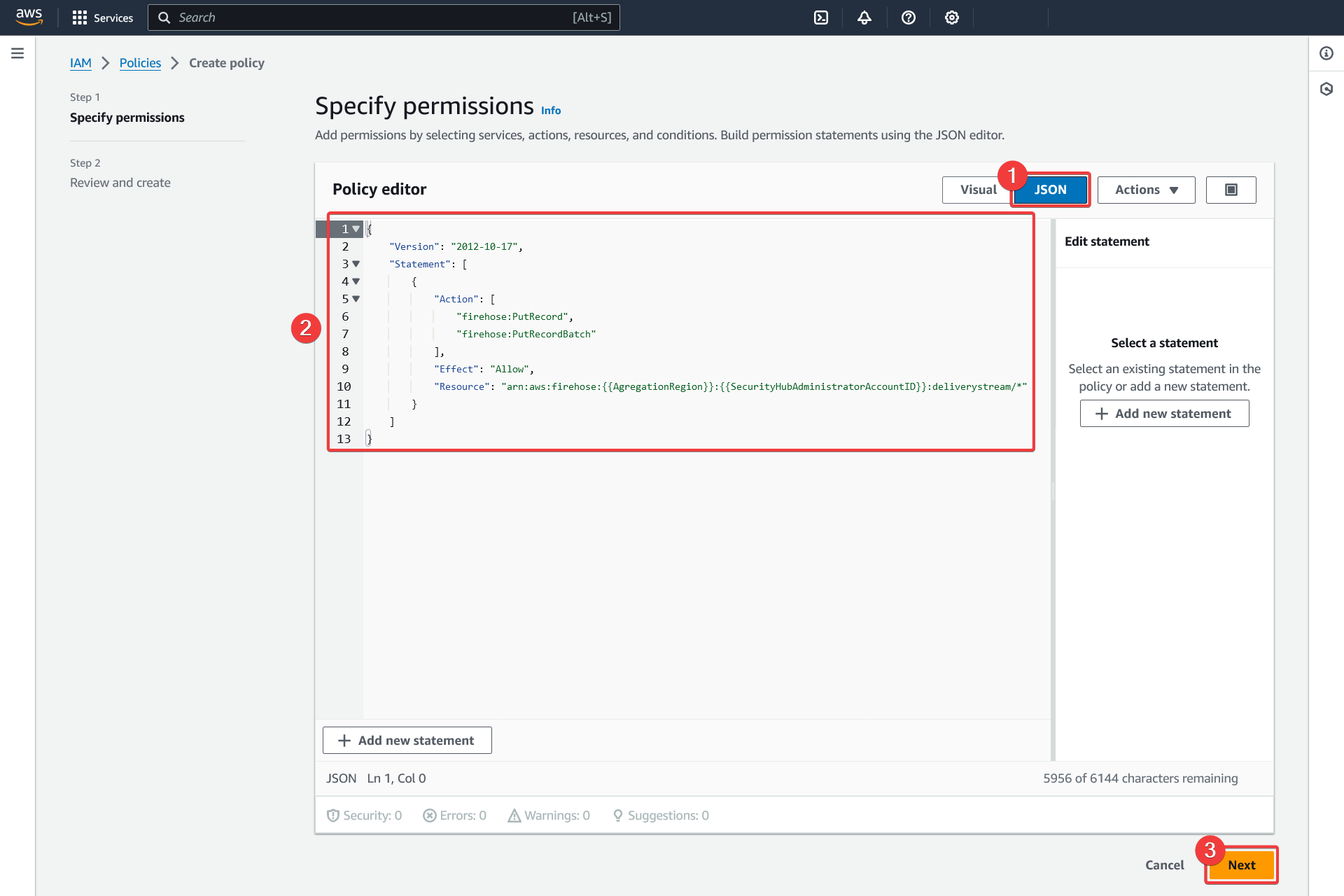
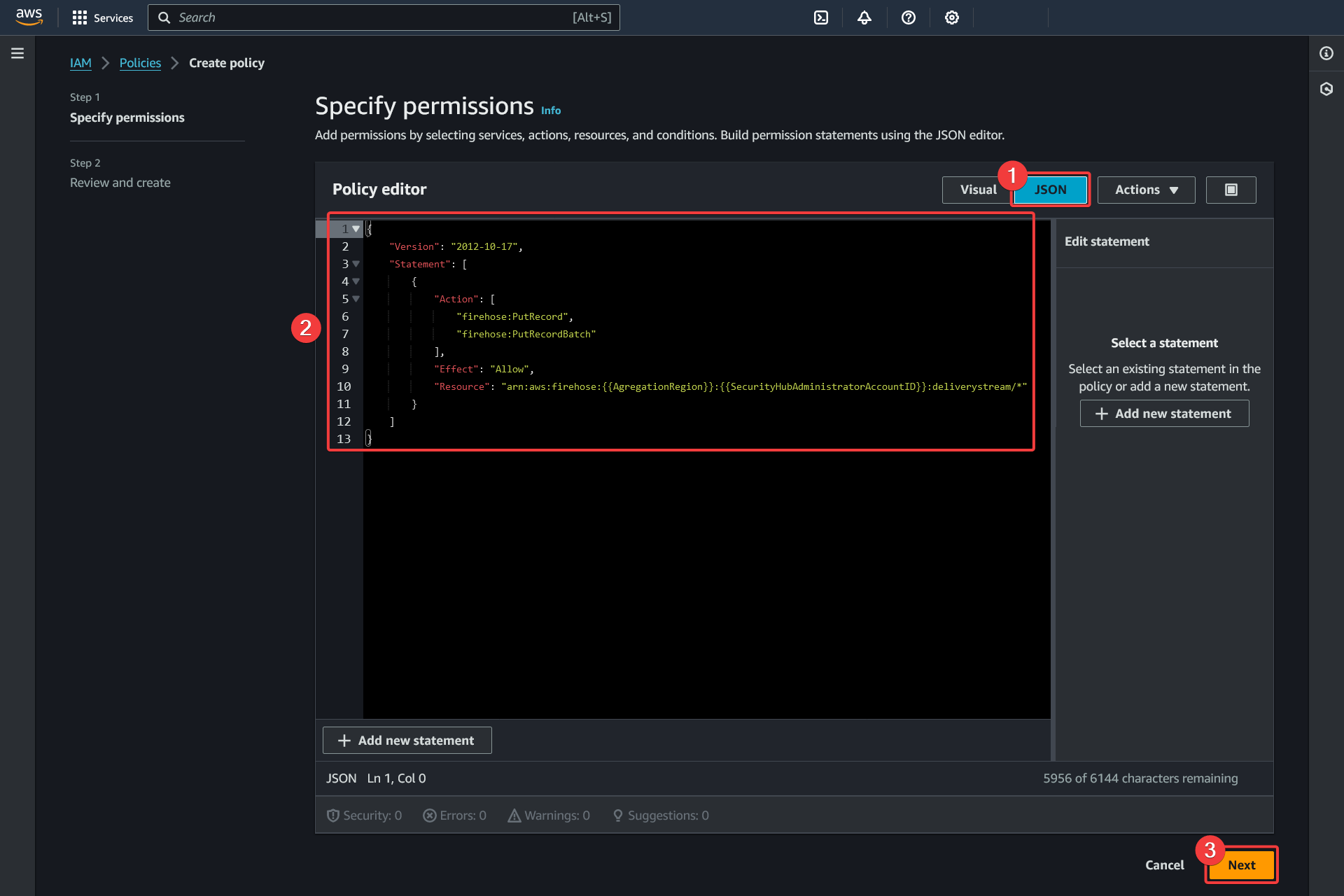
Create policy - Specify permissions
-
Click on the "JSON" tab
-
Use the following policy template
Replace the following values:
{{AggregationRegion}}: the name of the aggregation region{{SecurityHubAdministratorAccountID}}: the Security Hub administrator account number
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"firehose:PutRecord",
"firehose:PutRecordBatch"
],
"Effect": "Allow",
"Resource": "arn:aws:firehose:{{AggregationRegion}}:{{SecurityHubAdministratorAccountID}}:deliverystream/*"
}
]
}
This policy will give CloudWatch the right to write to all "Kinesis Firehose delivery streams". You can restrict access to the previously created delivery stream by changing the "ARN" key of the resource.
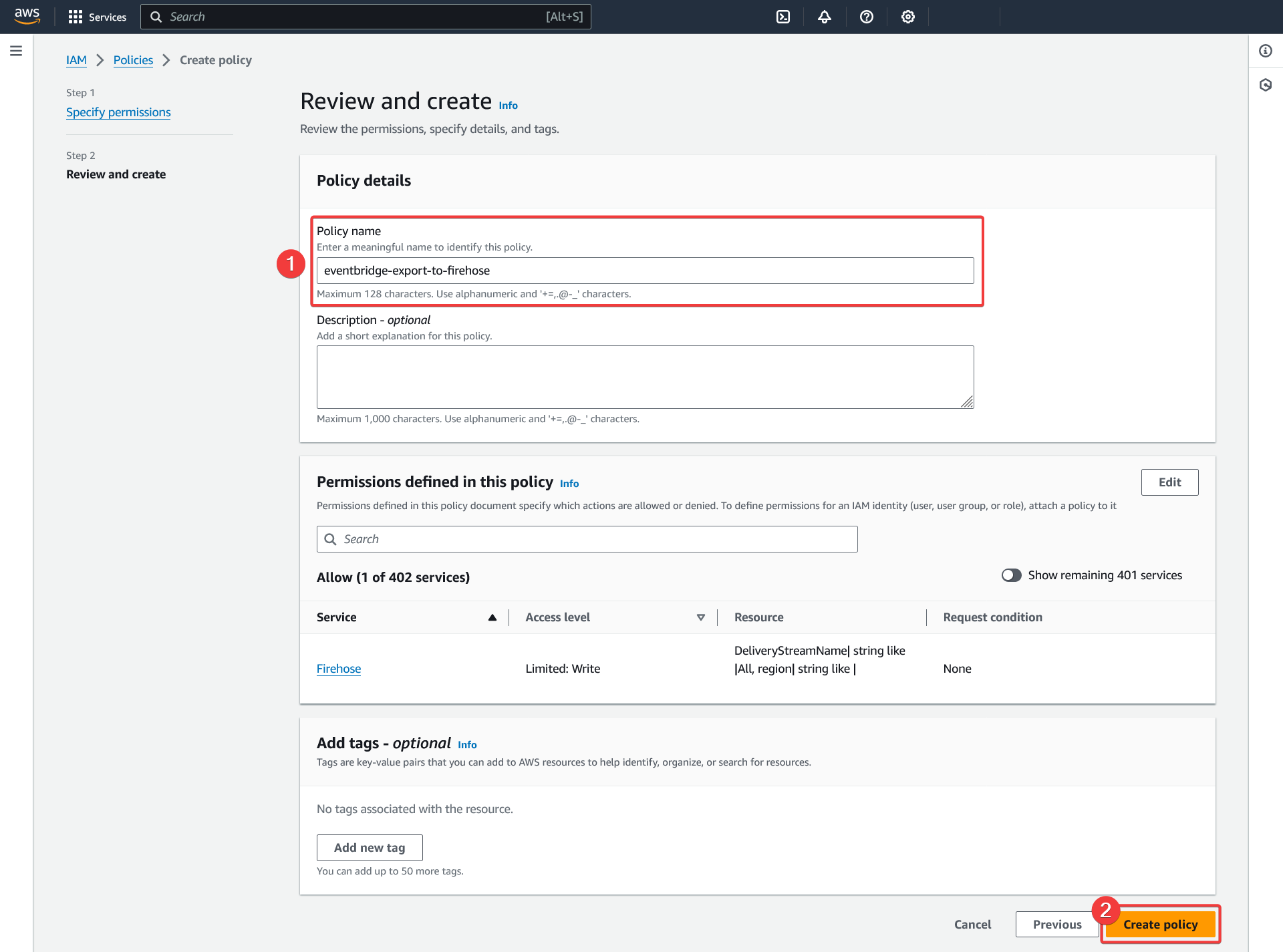
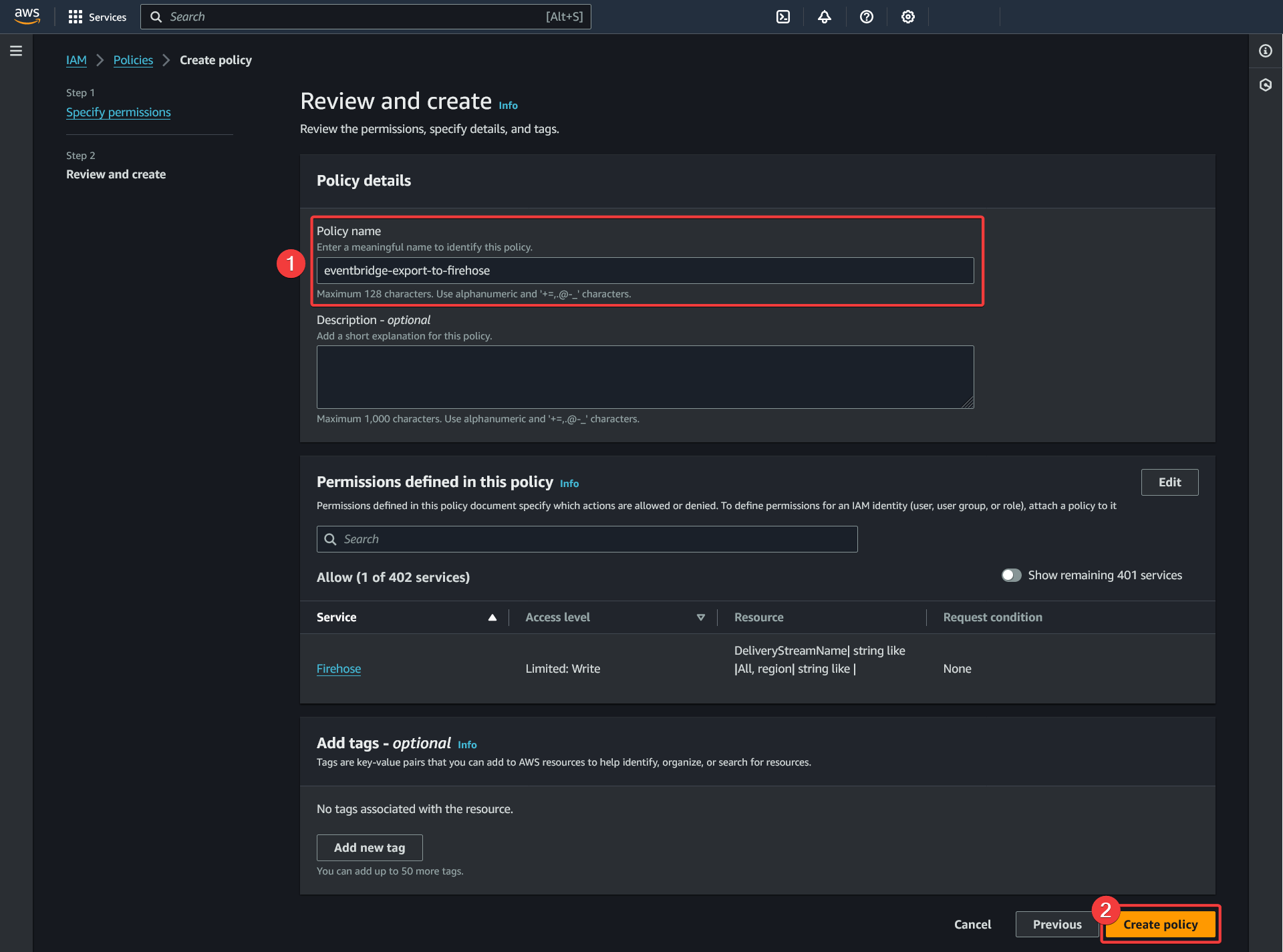
Create policy - Review and create
- Choose a descriptive name for the policy and take it in note for the IAM role we will create
- Click "Create policy"
Creating an IAM role for CloudWatch
- Go to the "Roles" section of the IAM service
- Click "Create role"
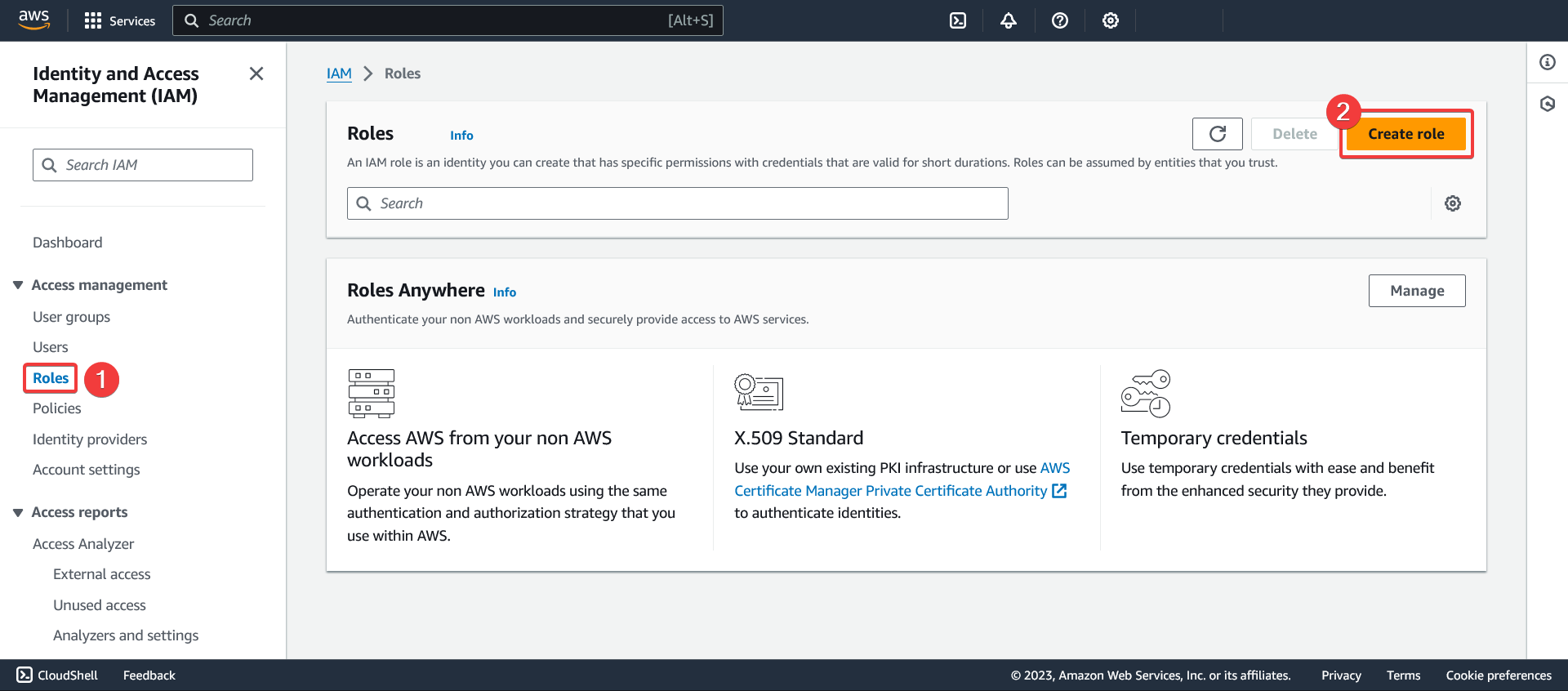
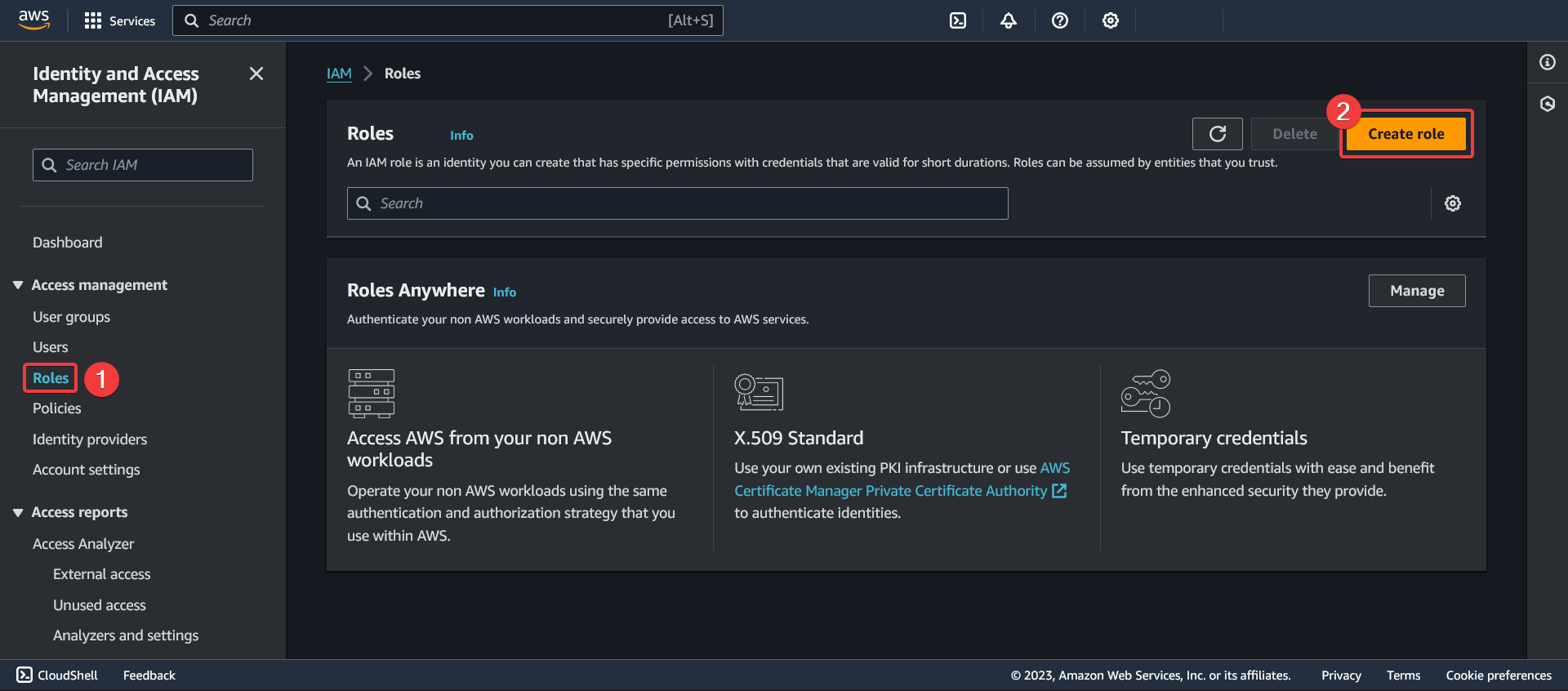
Select a trusted entity
- Select the "AWS Service" trusted entity type
- Select the "Kinesis" service
- Select the "Kinesis Firehose" use case
- Click "Next"
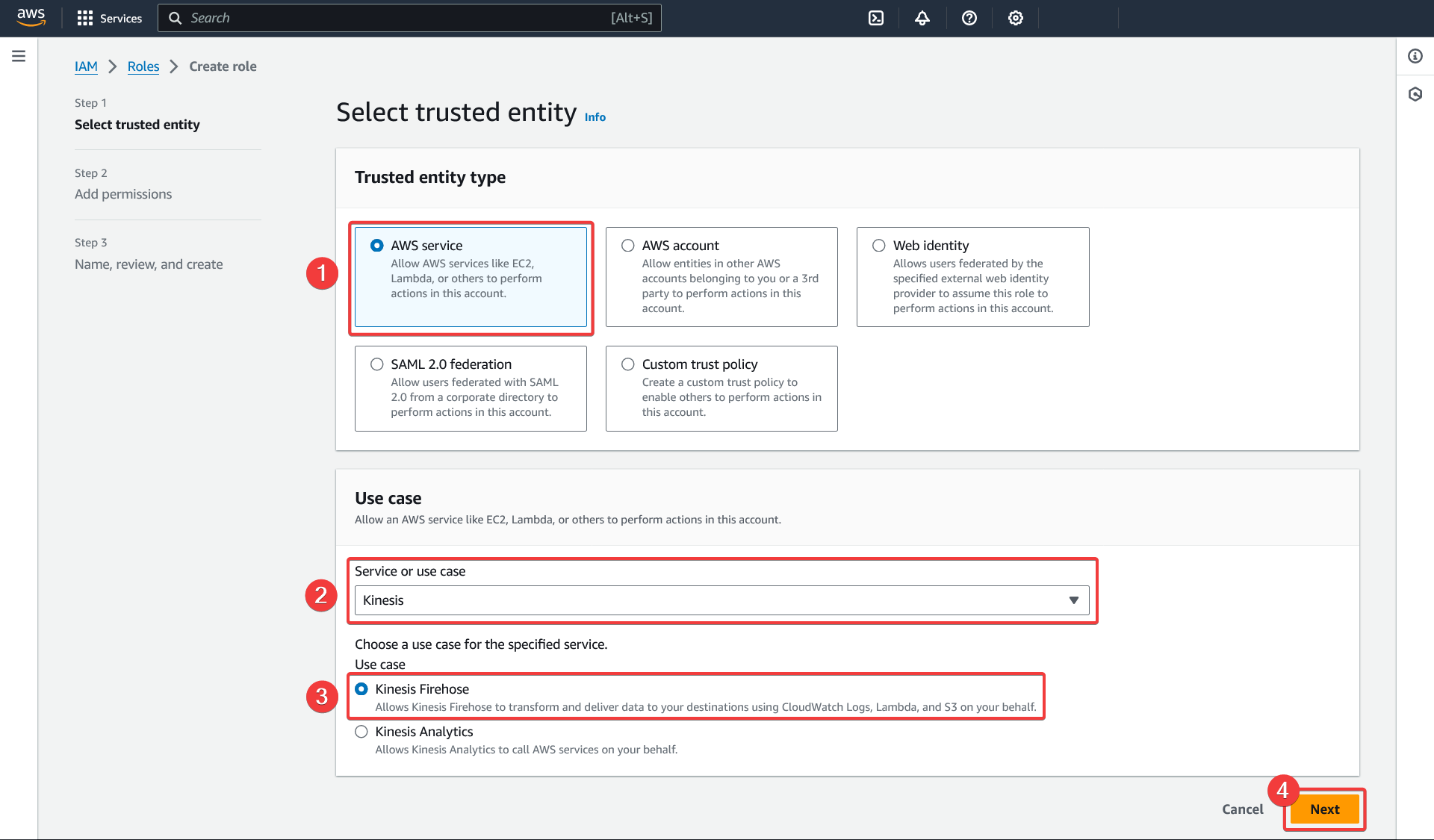
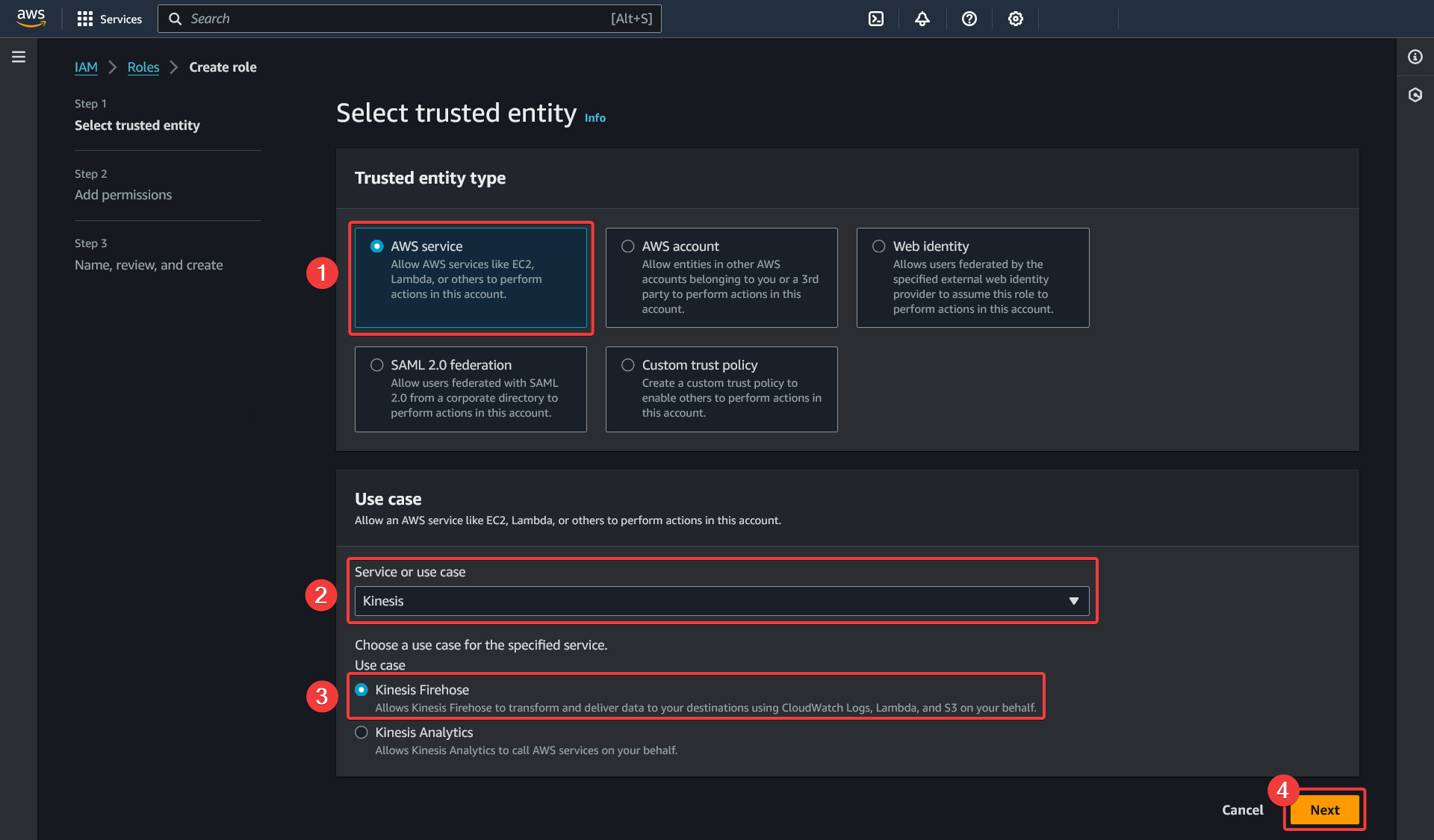
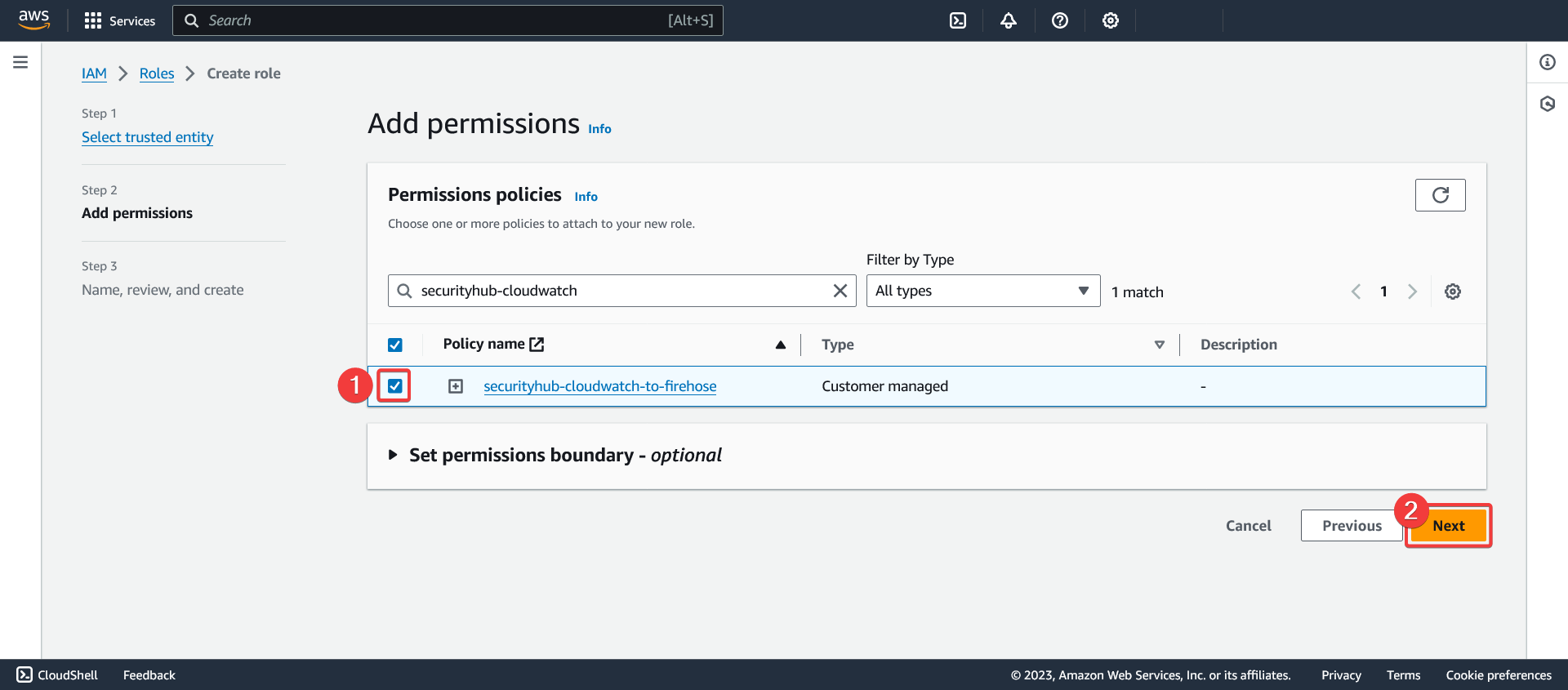
Add permissions
- Check the new policy
- Click "Next"
Name, check and create
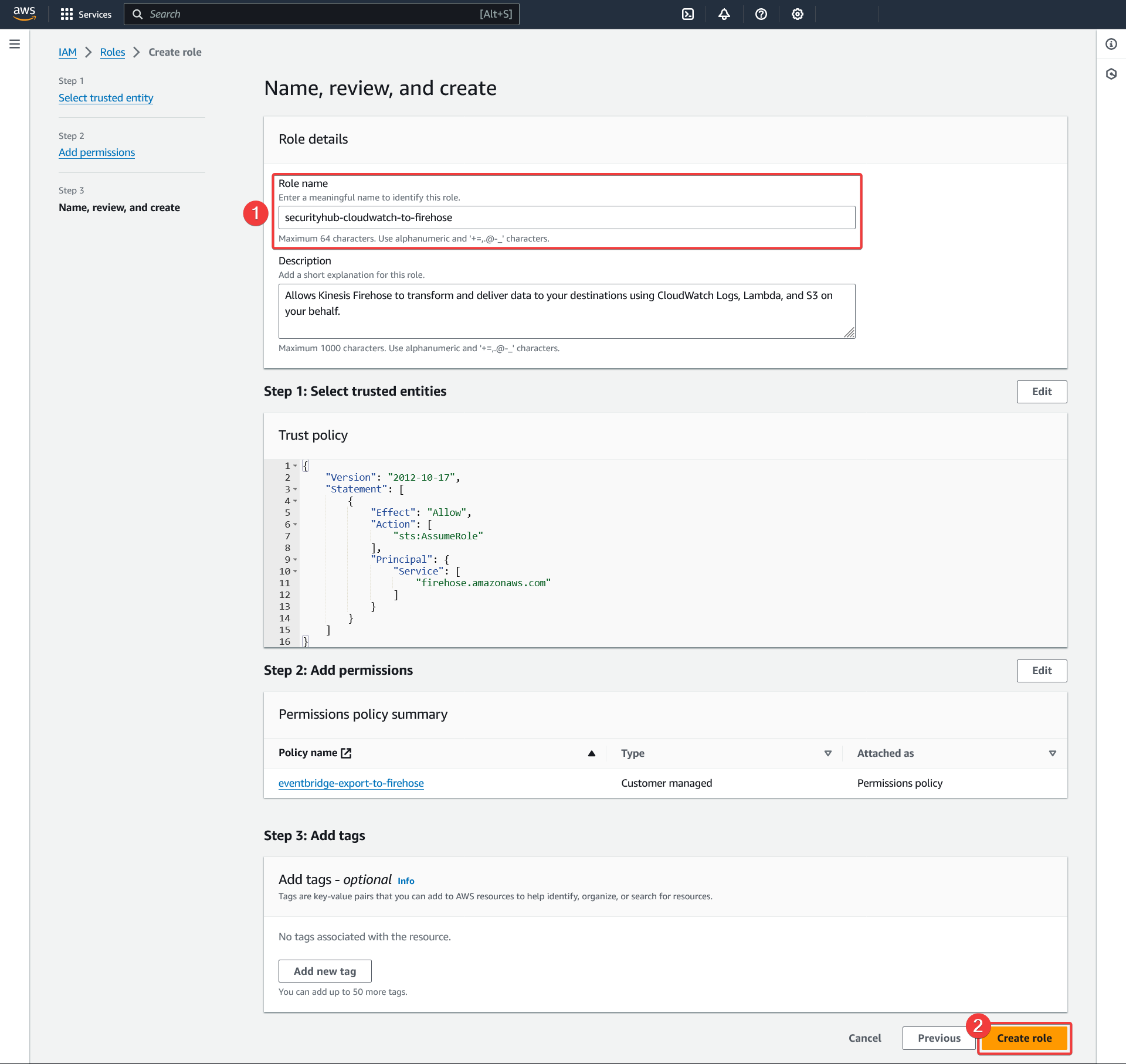
- Choose a descriptive role name and keep it noted for the Kinesis Firehose subscription filter creation
- Click "Create role"
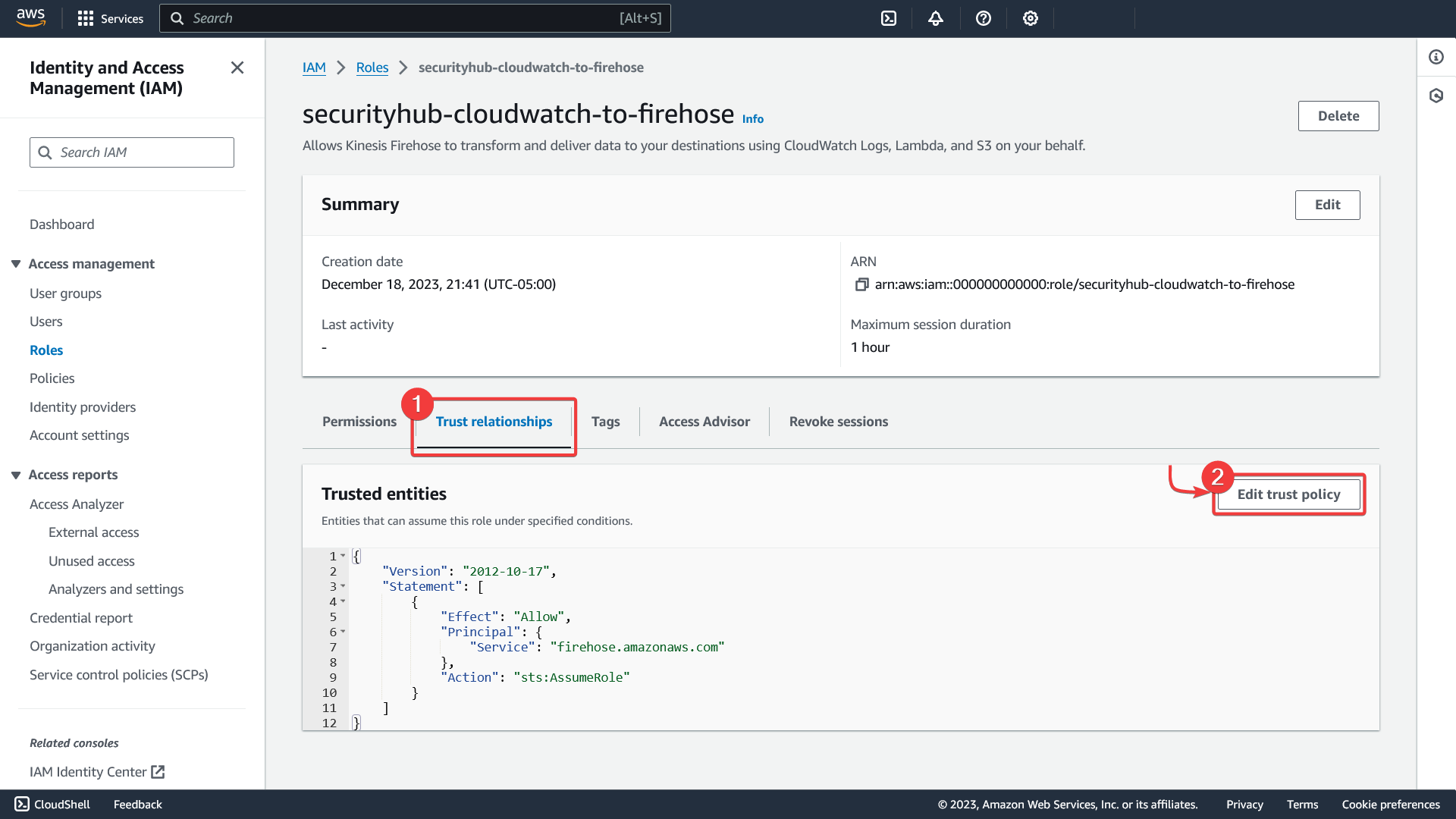
Delegate role to CloudWatch service
- On the new role page, click the "Trust relationships" tab
- Click "Edit trust policy"
Replace the policy with the following template.
Replace the following values:
{{AggregationRegion}}: the name of the aggregation region{{SecurityHubAdministratorAccountID}}: the Security Hub administrator account number
{
"Version": "2008-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "logs.{{AggregationRegion}}.amazonaws.com"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringLike": {
"aws:SourceArn": "arn:aws:logs:{{AggregationRegion}}:{{SecurityHubAdministratorAccountID}}:*"
}
}
}
]
}
Save to complete the role configuration.
Creating the Kinesis Firehose subscription filter
- In CloudWatch, go to the "Log groups" section
- Find the log group created earlier and click on it to view its details
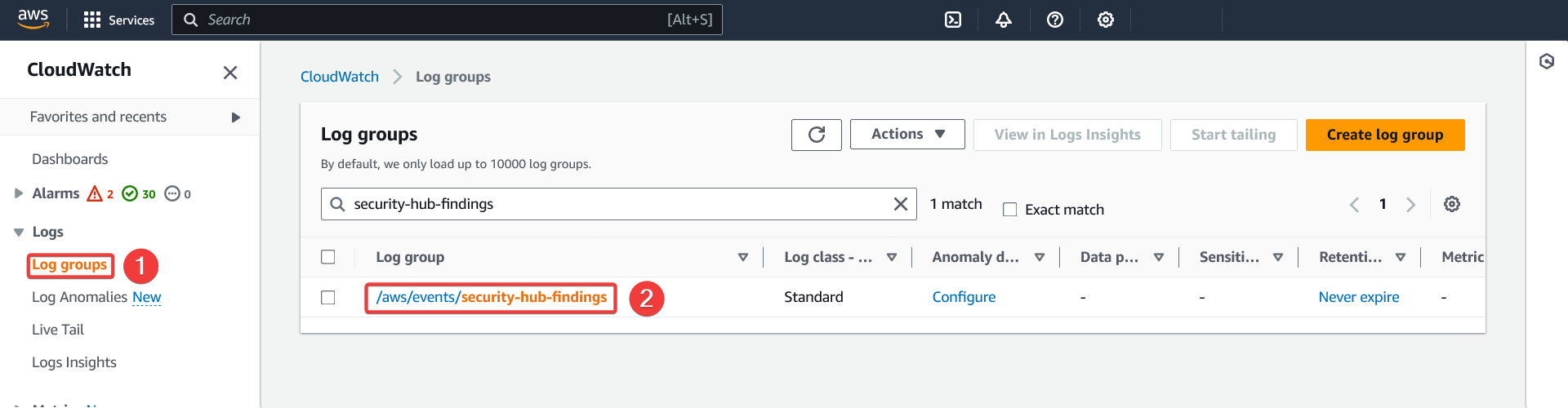
Log group details
- Click on the "Subscription filters" tab
- Click on the "Create" button
- Select "Create Kinesis Firehose subscription filter"
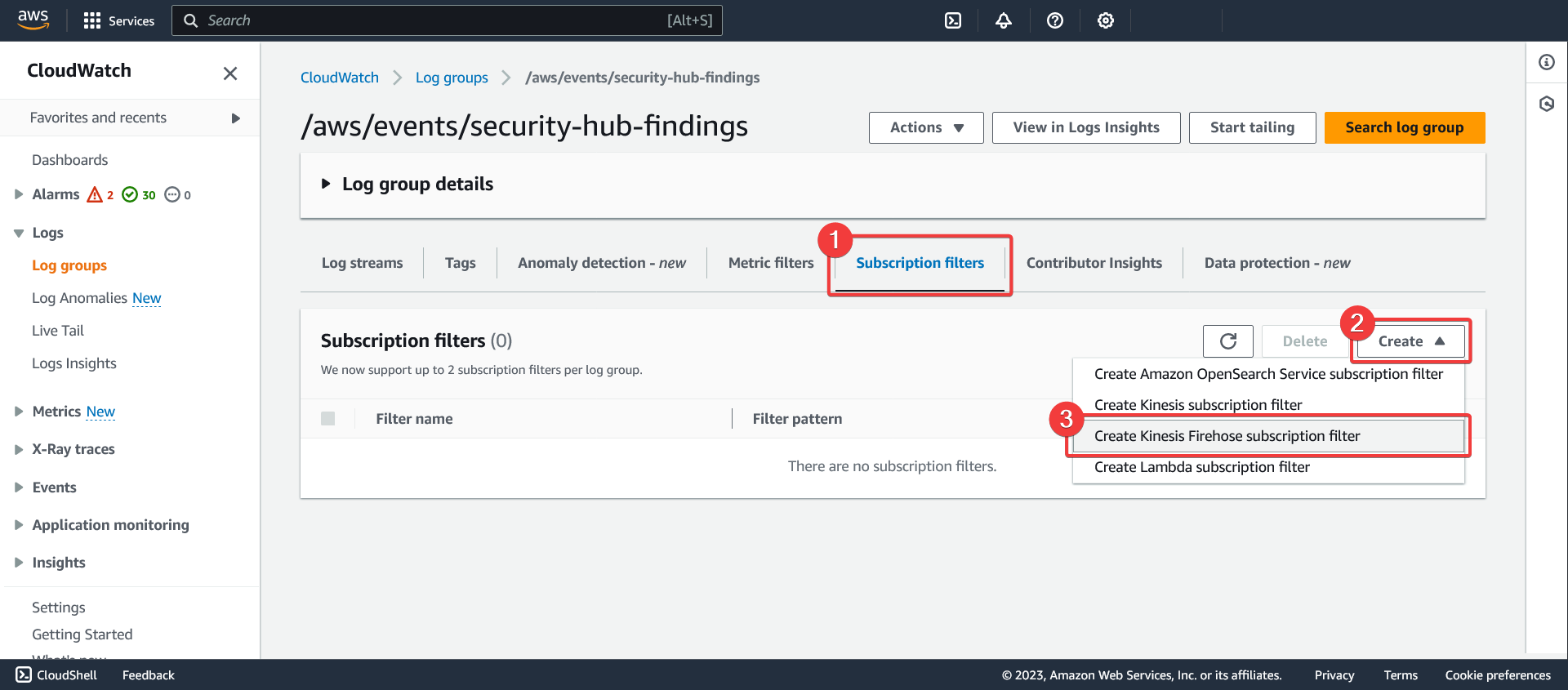
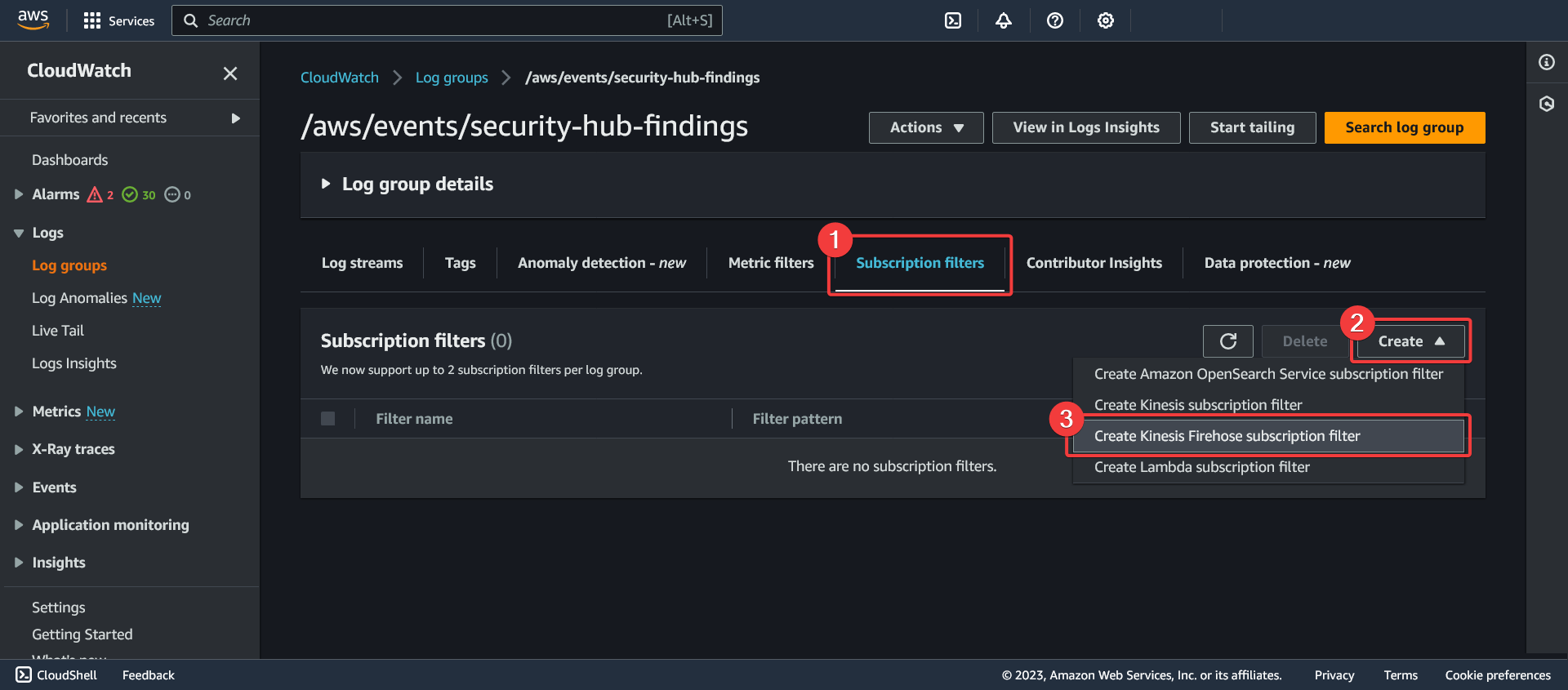
Create a Kinesis Firehose subscription filter for the log group
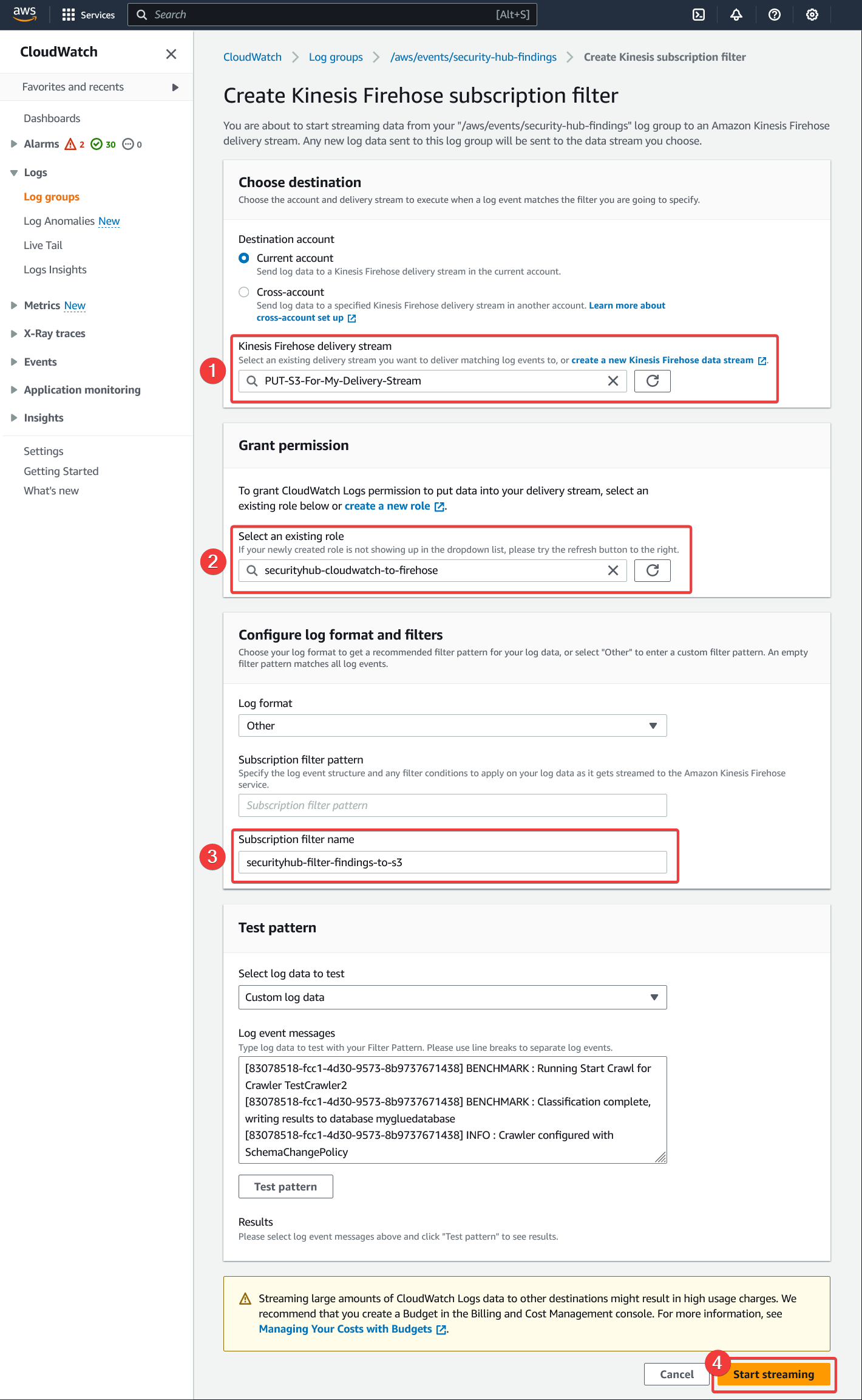
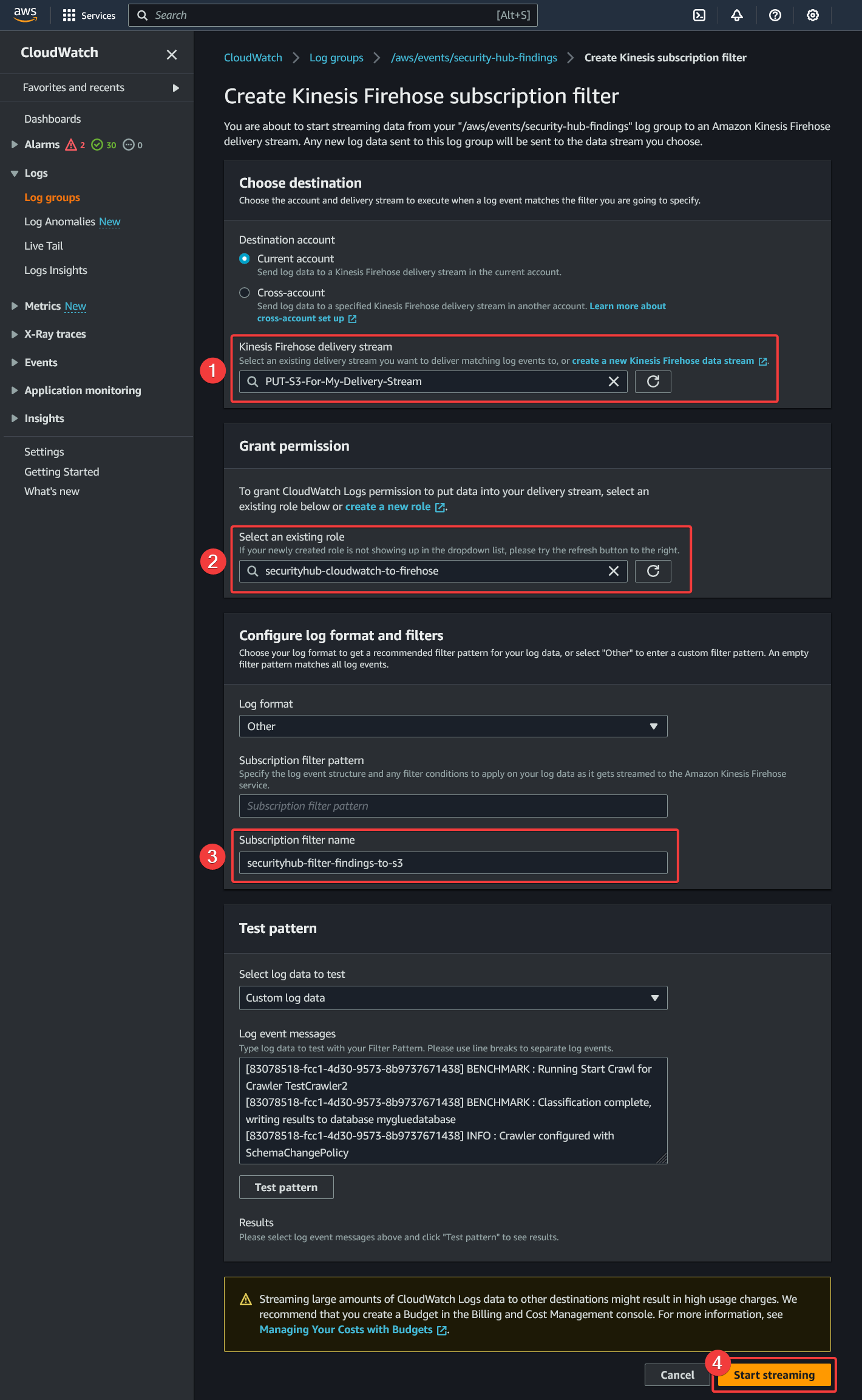
- Select the "Kinesis Firehose delivery stream" created earlier
- Select the role created earlier
- Give the subscription filter a descriptive name
- Click "Start streaming"
If you get an error during creation, make sure the role has the correct permissions.
AWS - CloudWatch - Log Groups - Subscription Filters - Create Kinesis Firehose subscription filter
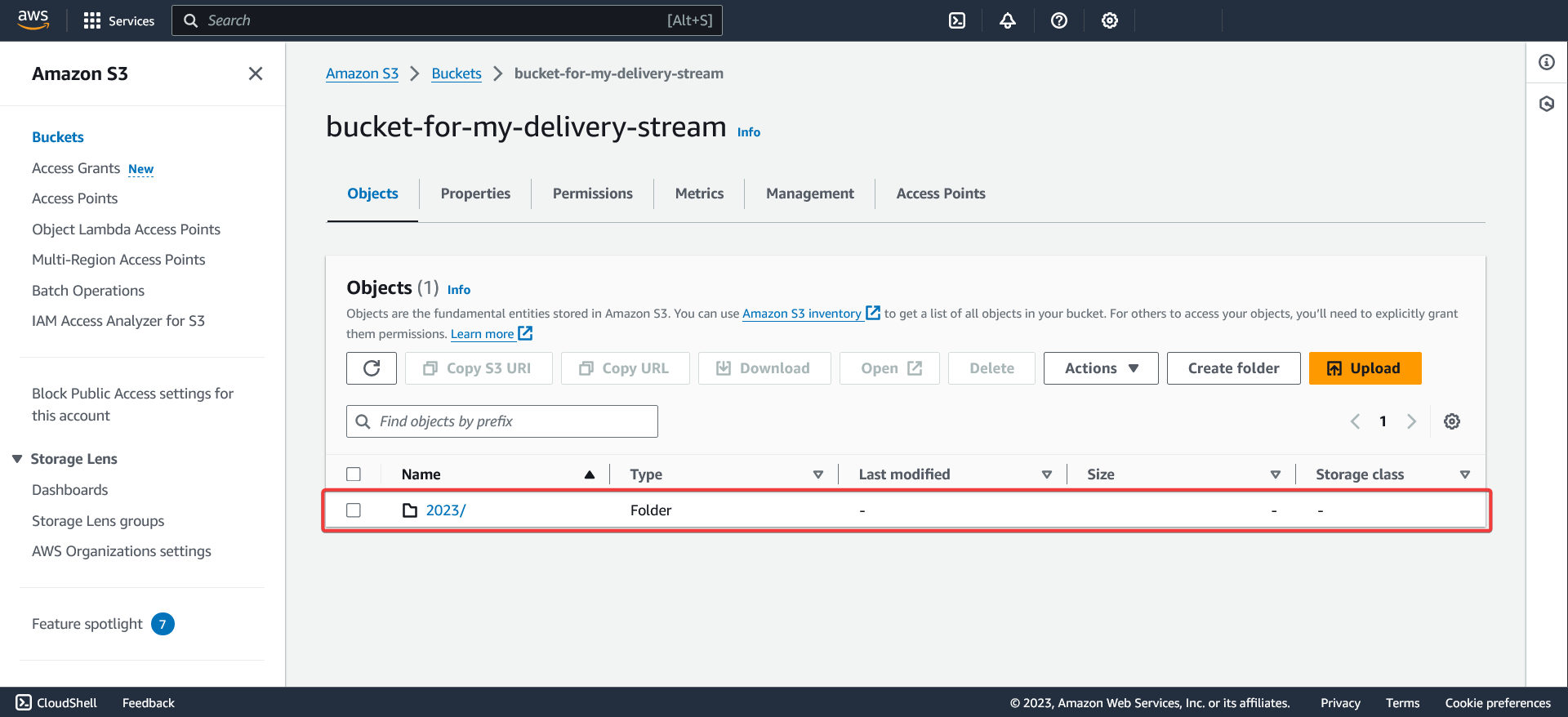
Verifying the installation
The configuration will be valid if control events appear in the S3 bucket. Propagation is not instantaneous between services and may take some time. The expected result is a Year/Month/Day/Time directory tree which will include the compressed files of the findings generated by Security Hub.
Notify Mondata with instance information
Include the following information:
{{S3SecurityHubAuditBucketName}}