Microsoft 365 Sign-ins
Microsoft Entra logs all sign-ins into an Azure tenant, which includes your internal apps and resources. [...] Reviewing sign-in errors and patterns provides valuable insight into how your users access applications and services.
To learn more about the service see the Microsoft Entra sign-in logs documentation.
Prerequisites
Setup
- M365 audits enabled: Enable or disable auditing functionality
Permissions
- “General Administrator” role in Azure AD
- “Organization Admin” role in MD.ECO
- Microsoft 365 auditing activated: Turn auditing on or off | Microsoft Learn
Configuration steps
Registering an application for the connector
Required configuration
- General settings
- Name: MD.ECO - Connector - Microsoft 365 (Signins + Office)
- Supported account types: accounts in this organizational directory only (default option)
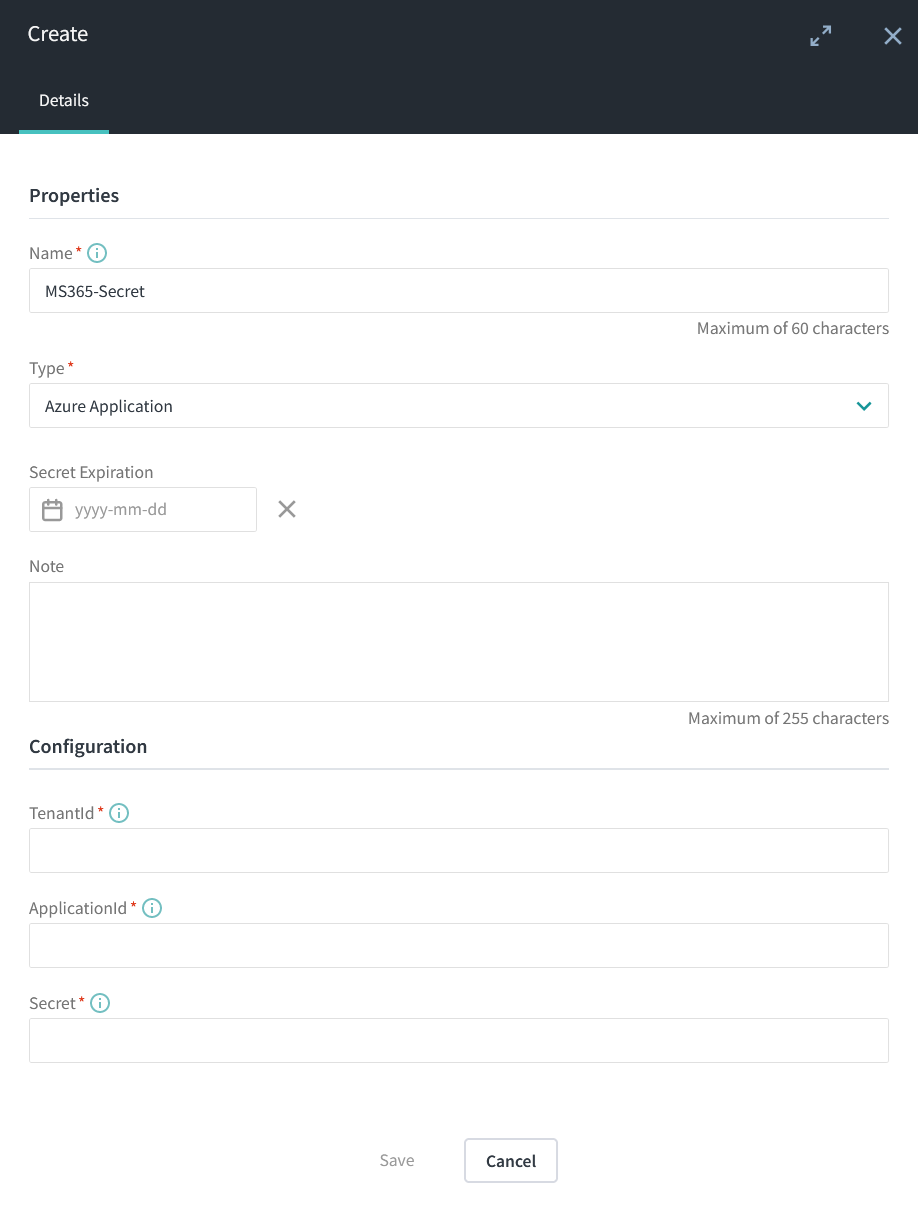
- A secret
- API permissions required
- See the following section
API permissions required
Microsoft Graph (4)
| Permission Name | Permission Type | Description |
|---|---|---|
| AuditLog.Read.All | Application | Read all audit log data |
| Policy.Read.ConditionalAccess | Application | Read applied Conditional Access policies |
| Reports.Read.All | Application | Read all usage reports |
| User.Read.All | Application | Read all users' full profiles |
Office 365 Management APIs (2)
| Permission Name | Permission Type | Description |
|---|---|---|
| ActivityFeed.Read | Application | Read activity data for your organization |
| ActivityFeed.ReadDlp | Application | Read DLP policy events including detected sensitive data |
Step by Step Steps
- Microsoft reference documentation: Quickstart: Register an application in the Microsoft identity platform - Microsoft Entra | Microsoft Learn
- Register the application
- Add API Permissions
- Administrator consent
- Add a Secret
Create Azure application secret in MD.ECO