Microsoft 365 Defender
Microsoft Defender for Office 365 helps organizations secure their enterprise with a set of prevention, detection, investigation, and hunting capabilities to protect emails and Office 365 resources.
To learn more about the service see the documentation on Microsoft 365 Defender.
Prerequisites
Permissions
- "Global Administrator" role in Azure AD
- "Organization Admin" role in MD.ECO
- At least one Microsoft 365 Defender module configured and licensed
- Microsoft Defender for Endpoint
-
Defender for Endpoint Plan 2 licenses
or
-
Defender for Business licenses
or
-
Defender for Cloud - Defender for Server Plan 2 licenses
-
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Defender for Office 365 Plan 2 licenses
- Microsoft Defender for Cloud Apps
- Microsoft Data Loss Prevention
- Microsoft Defender for Endpoint
Configuration Steps
Registering an application for the connector
Required Configuration
- General settings
- Name: MD.ECO - Connector - M365 Defender
- Supported account types: Accounts in this organizational directory only (default option)
- One secret
- Required API permissions
Required API permissions
Microsoft Graph (2)
| Permission Name | Permission Type | Description |
|---|---|---|
| User.Read.All | Application | Read user profile information |
| SecurityIncident.ReadWrite.All | Application | Read and write to all security incidents |
WindowsDefenderATP (6)
| Permission Name | Permission Type | Description |
|---|---|---|
| Machine.Read.All | Application | Read all machine profiles |
| Vulnerability.Read.All | Application | Read vulnerability information for threat and vulnerability management |
| Software.Read.All | Application | Read software information for threat and vulnerability management |
| User.Read.All | Application | Read user profile information |
| AdvancedQuery.Read.All | Application | Execute advanced queries |
Step-by-Step Guide
- Microsoft reference documentation: Quickstart: Register an application in the Microsoft identity platform - Microsoft Entra | Microsoft Learn
- Register the application
- Add API Permissions
- Administrator consent
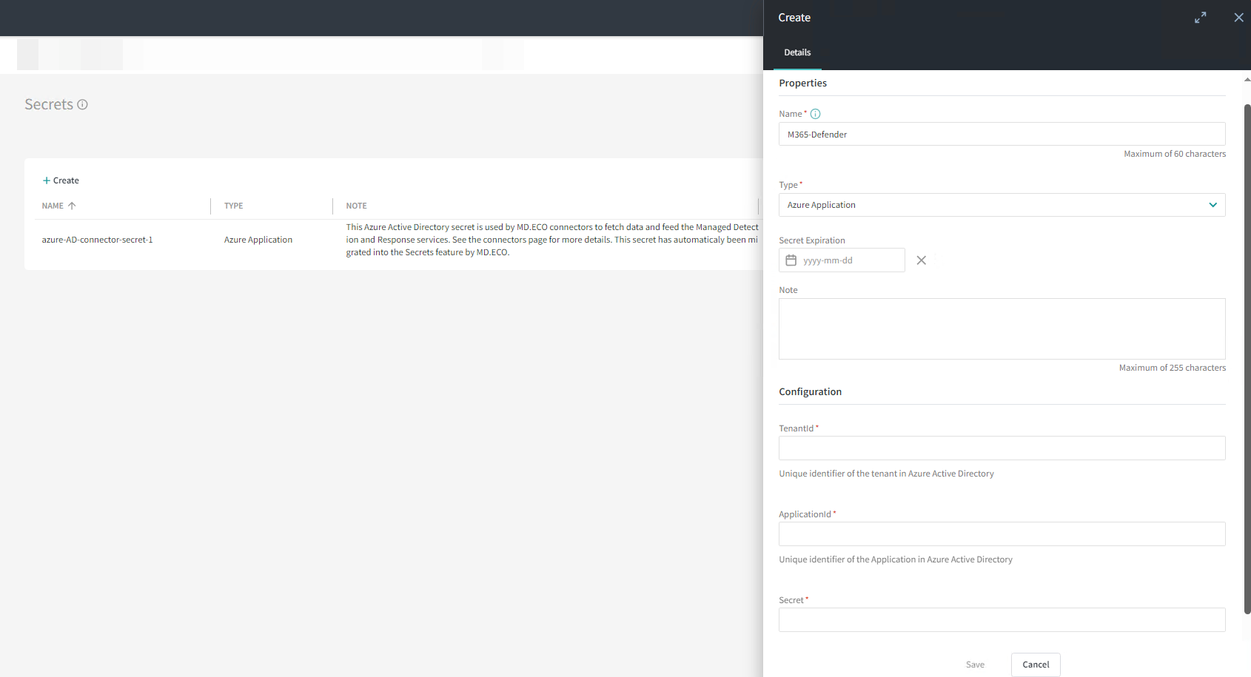
- Add a Secret
(Optional) Registering a remediation application [Beta]
It is possible to register a new application to separate remediation rights from the base application for the connector. It's also possible to simply add the required permissions in the same application.
Required Configurations
- General settings
- Name: MD.ECO - Connector - Microsoft 365 Defender - Remediation
- Supported account types: Accounts in this organizational directory only (Default option)
- One secret
- Remediation API permissions
Remediation API permissions
Microsoft Graph (1)
| Permission Name | Permission Type |
|---|---|
| User.ReadWrite.All | Application |
WindowsDefenderATP (2)
| Permission Name | Permission Type |
|---|---|
| Machine.Isolate | Application |
| Machine.Scan | Application |
Create the Azure application secret in MD.ECO and notify Mondata when completed