Microsoft Sentinel
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
To learn more about the service see the Microsoft Sentinel documentation.
Prerequisites
Permissions
- "General Administrator" role in Azure AD
- "Organization Admin" role in MD.ECO
- "Owner" role of the resource group or subscription that contains the Azure Sentinel deployment
Configuration steps
Registering an application for the connector
System requirements
- General settings
- Name: MD.ECO - Connector - Microsoft Sentinel
- Supported account types: accounts in this organizational directory only (default option)
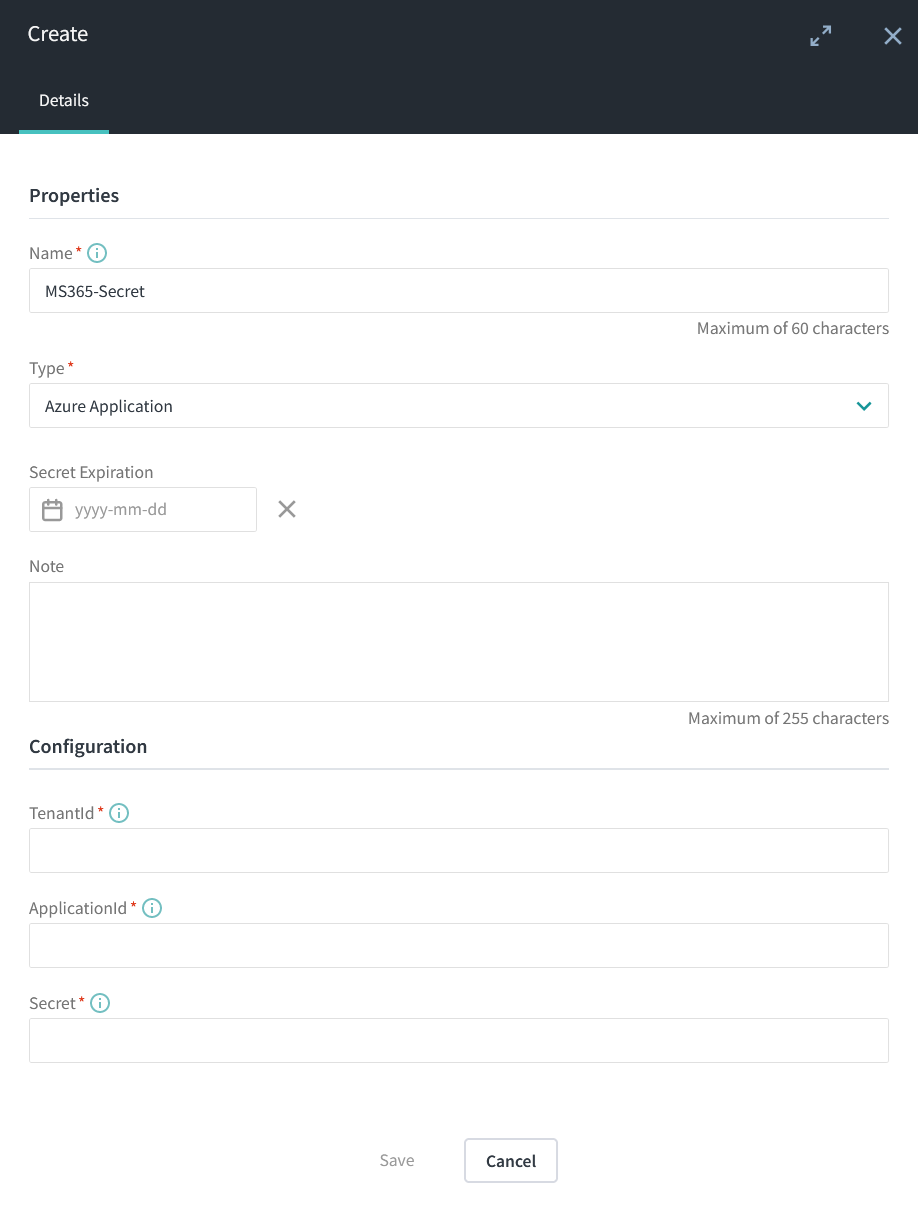
- A secret
- API permissions required
- No Permissions required in Azure AD
Step by Step Steps
- Microsoft reference documentation: Quickstart: Register an application in the Microsoft identity platform - Microsoft Entra | Microsoft Learn
- Register the application
- Add API Permissions
- Administrator consent
- Add a Secret
Create the Azure application secret in MD.ECO
Assigning the Azure Sentinel Reader role to the application
In the resource group where Azure Sentinel is deployed, assign Microsoft Sentinel Reader role to the application created in the previous step
Microsoft documentation: Tutorial: Grant a user access to Azure resources using the Azure portal
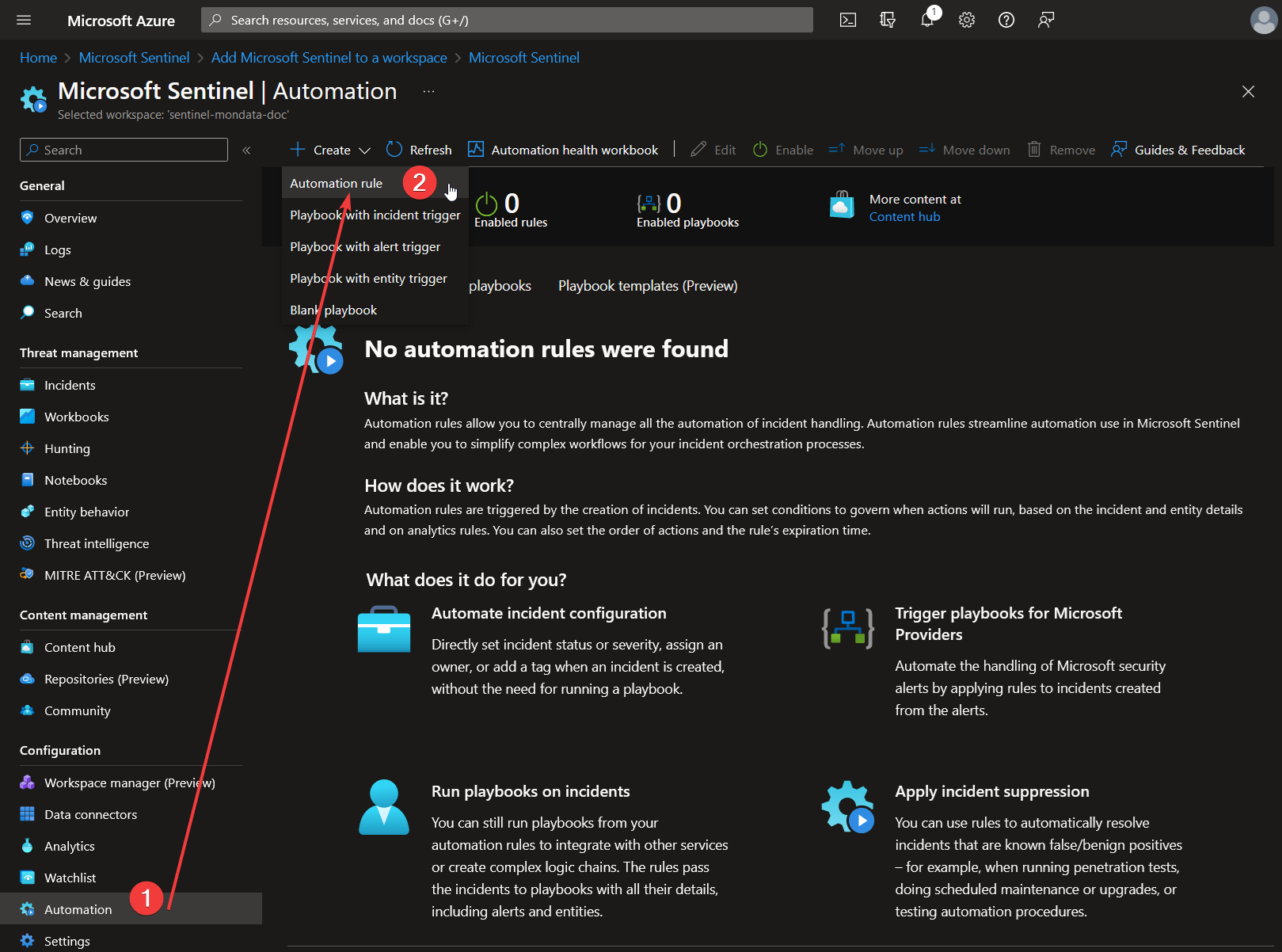
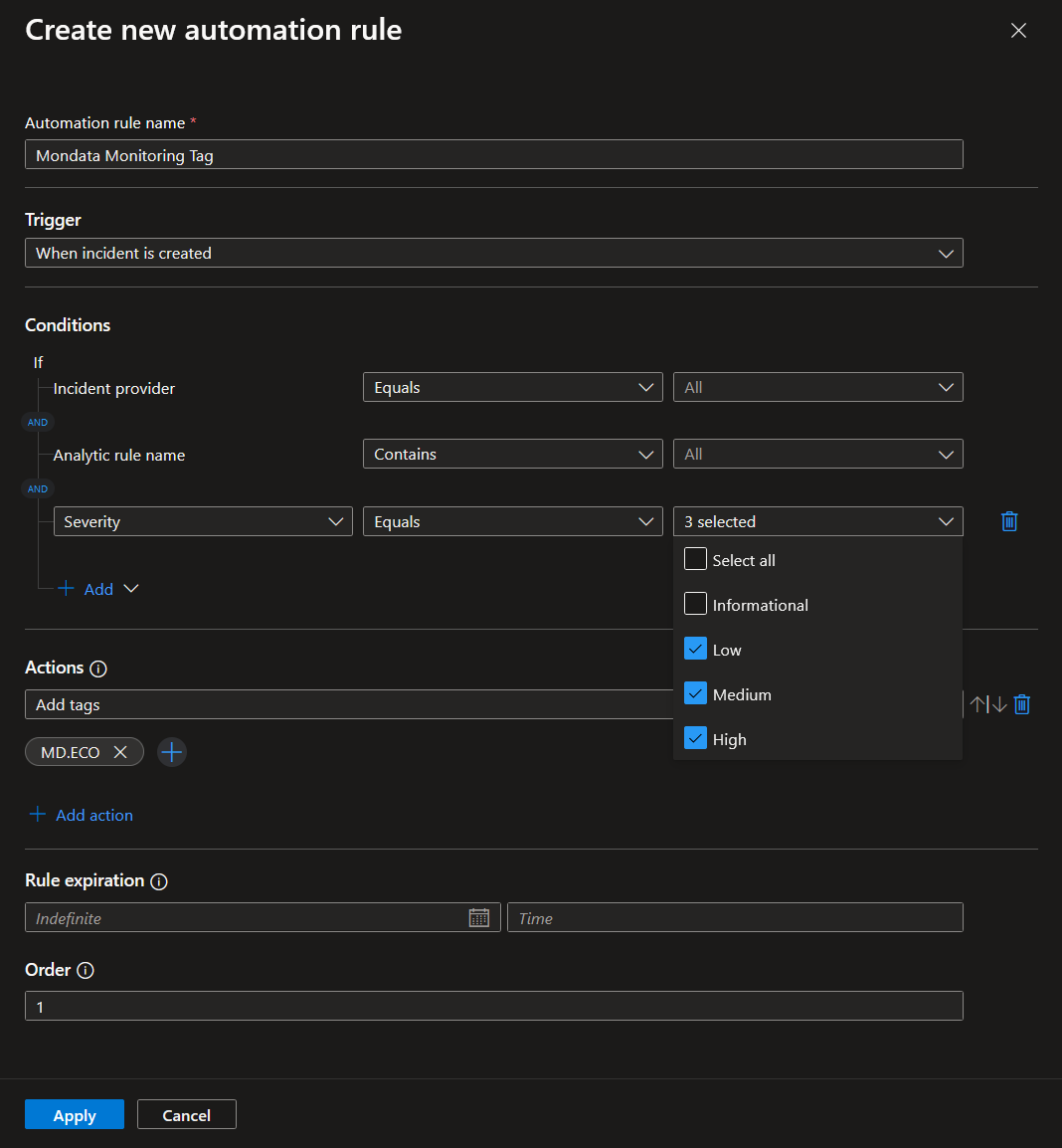
Creation of a “Tag Surveillance Mondata” automation rule
Although all incidents are retrieved and retained to aid investigation, only significant incidents are handled by the Mondata team. The use of a Tag allows you to make this filter within your environment and can be adjusted to add or remove incidents in collaboration with Mondata.
Microsoft documentation: Create and use Microsoft Sentinel automation rules to manage response
In your sentinel workspace, create a new rule
Adjust settings to reflect the following configuration
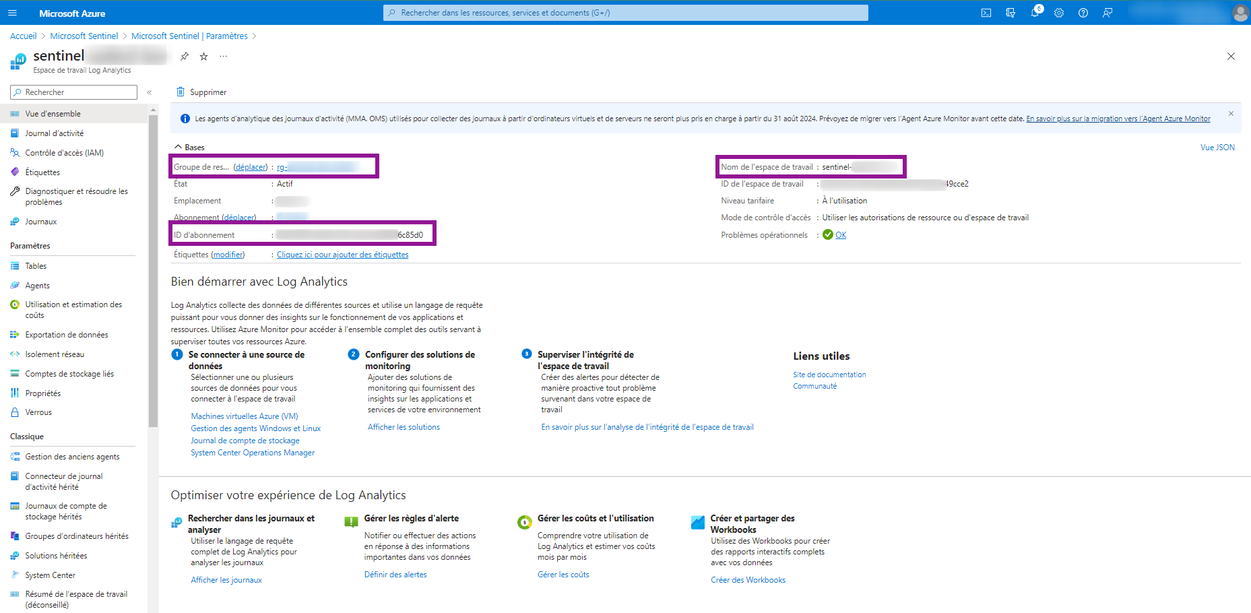
Notify Mondata with the instance information
Include the following information:
- Sentinel Resource Group Name
- Sentinel Workspace Name
- Azure subscription ID