Apply a Security Model
For a resource to be considered compliant, a model needs to be associated to it. This action is used to apply a security model on a resource.
Each model implements configurations such as:
- Channel visibility
- Folder structure
- Life cycle
- Permissions
The application consists of a few steps
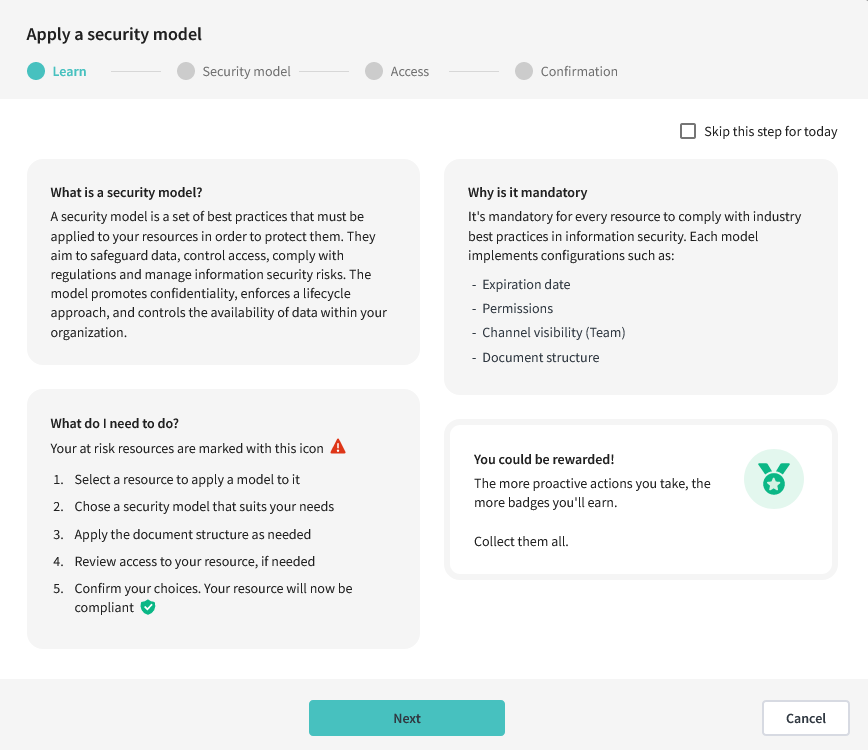
1. Learn
This step summarizes what security models are and why they are used. It can be skipped if you want to apply models to multiple resources in a short amount of time. You can always return to this step later if needed.
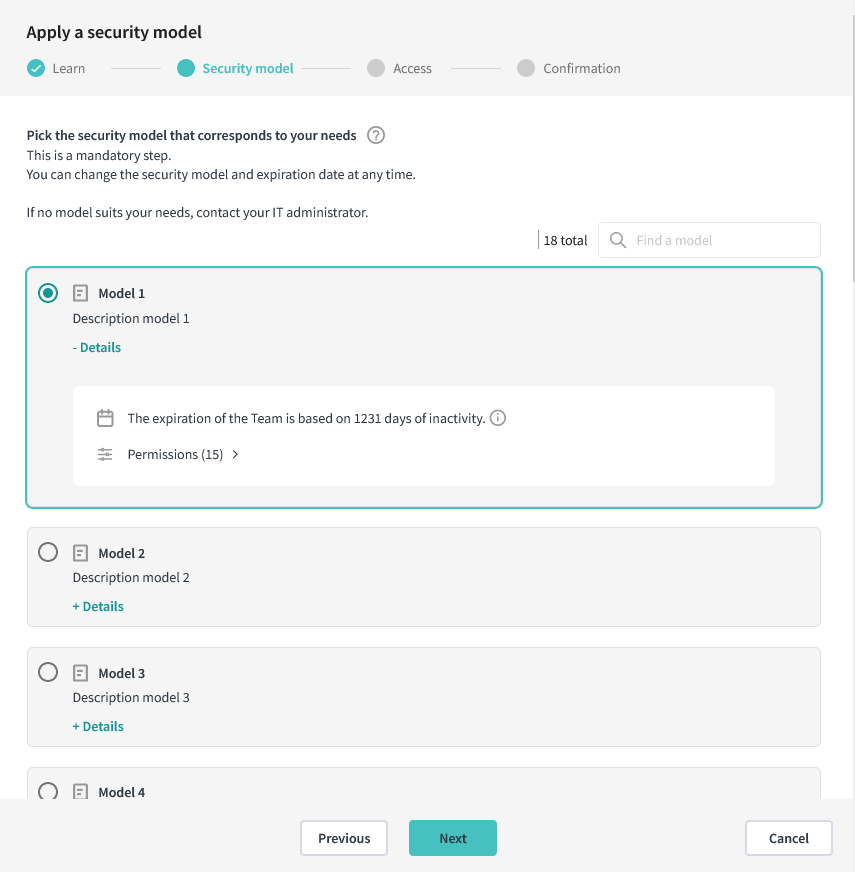
2. Selecting the security model
A list of models available to your organization is presented. Select a model that suits your needs best. Click on “Details” to see more information on the life cycle and the permissions defined by the model. Once your choice is made, press “Next”.
3. (Conditional) Applying the channel and folder structure
If the model you chose has a channel or a folder structure that can be applied to the resource, this step will appear.
You have the option to ignore the model’s channel and folder structure, which is set to be ignored by default. Click on the arrow to hide or expand the structure’s details.
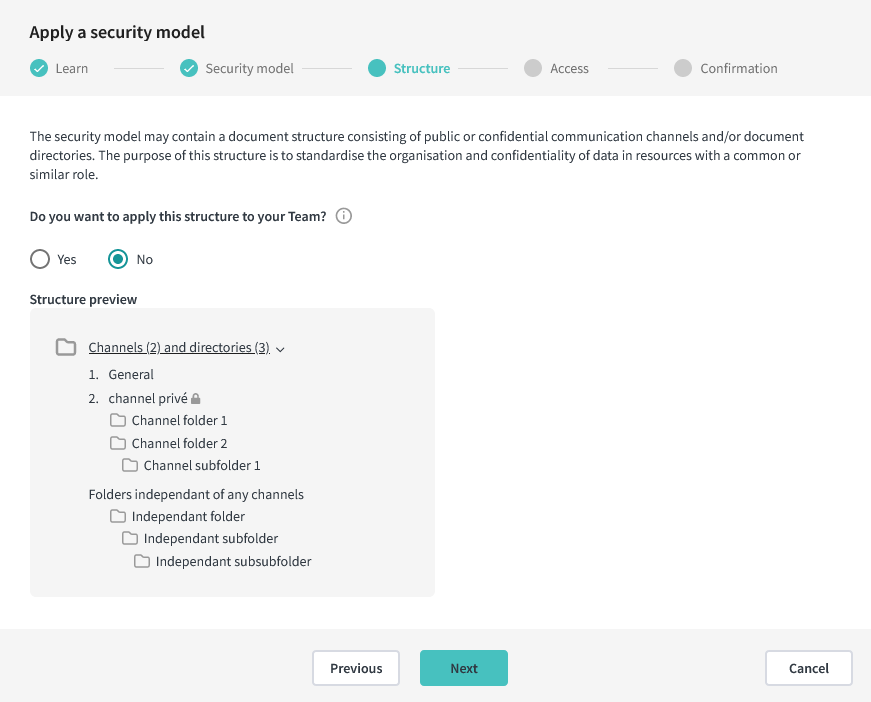
If you choose to apply the model’s channel and folder structure, existing channels and folders will not be impacted; channels with the same name will not be recreated, and conflicting files and folders won’t be recreated either.
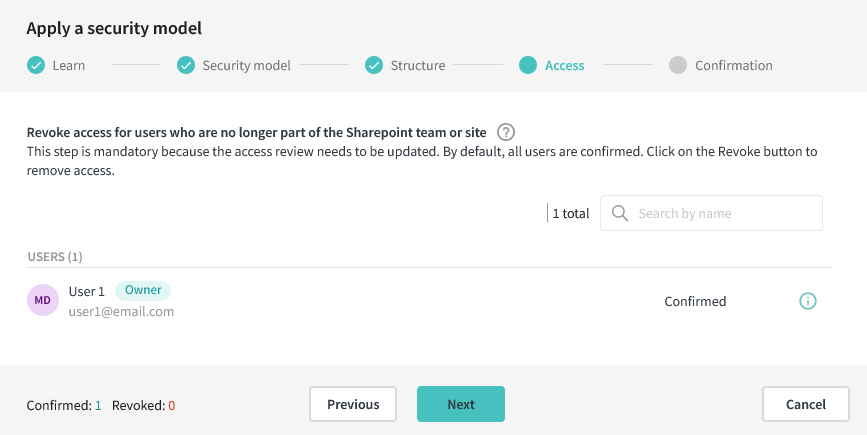
4. (Conditional) Review access
In the case where the resource you want to apply a model on needs its access reviewed, MD.ECO batches everything together for you and includes it in the model’s application steps.
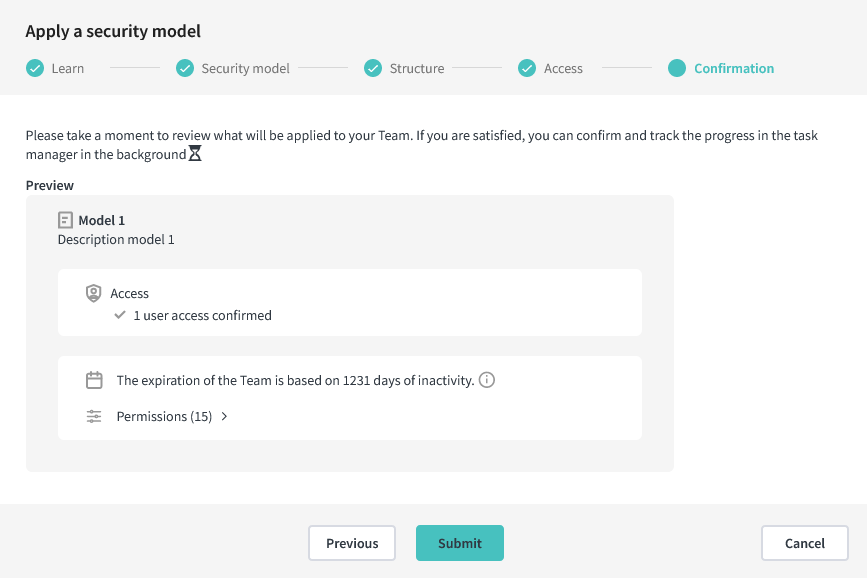
4. Confirmation
A summary of what will be applied to your group. Take the time to validate all the information is correct and corresponds to your needs.